NewStarCTF2023_Week5_WP
NewStarCTF2023-系列:
RE
两个字的开放世界游戏
beam文件的逆向,没见过,应该考信息搜集能力了
搜索一下可以了解到.beam是erlang编译过后的字节码文件
先大致学一下 erlang
大致了解后,上 erlang官网下载一下,配置一下环境。
再搜一下 .beam 的反汇编
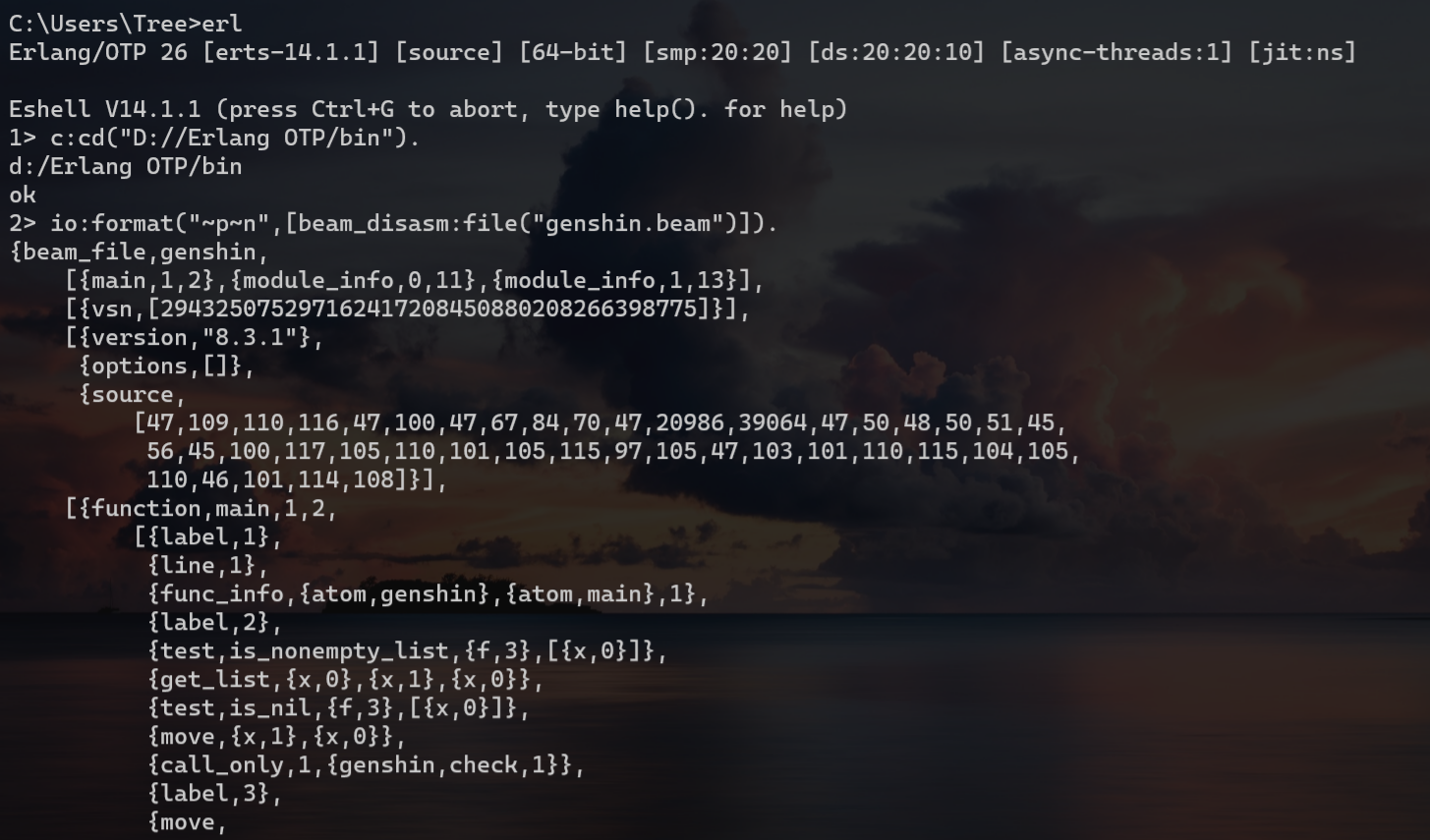
找到如下提取字节码命令。
1 | io:format("~p~n",[beam_disasm:file("genshin.beam")]). |
得到对应的字节码信息
1 | {beam_file,genshin, |
看起来有点长,大致能猜到意思
可以看到 main 里面调用了 check 来检验
function check 调用了transform,并且有一个{test,is_eq_exact
那么后面的<<107,114,102,103,130,68,118,106,107,119,88,109,131,70,114,130,122,81,111,40,107,77,76,38,52,73,72,101>>应该就是密文了。
观察一下function transform
应该是每一位和下标异或后加上4
据此写脚本梭
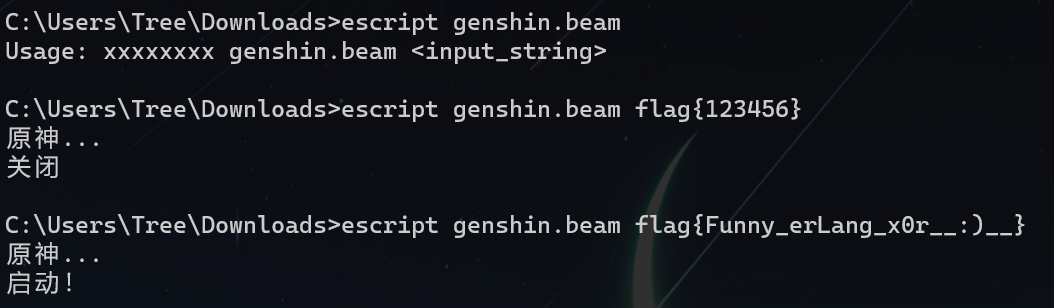
最后是可以用escript 命令将 .beam 文件以脚本形式运行来验证
exp
1 | enc = [107,114,102,103,130,68,118,106,107,119,88,109,131,70,114,130,122,81,111,40,107,77,76,38,52,73,72,101] |
flag
flag{Funny_erLang_x0r__:)__}
鱼
主函数分析失败,看看汇编
看到一堆 jz jnz花指令,手动patch
或者 idapython patch 一下
1 | start = 0x401530 |
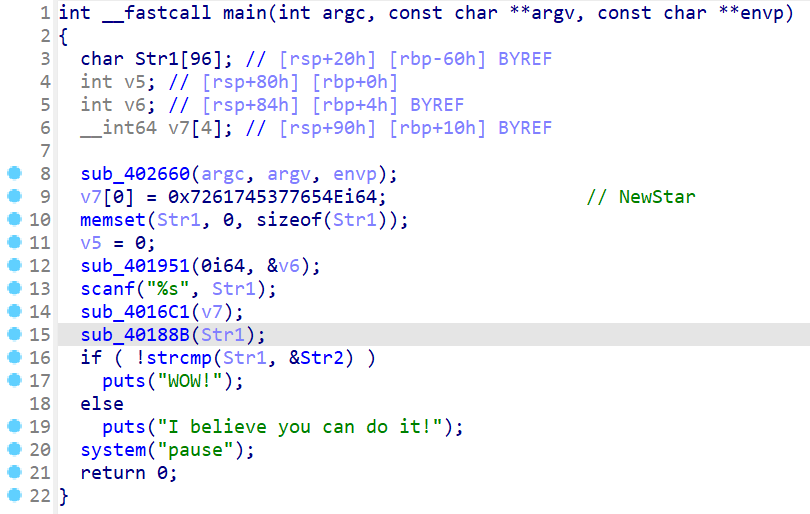
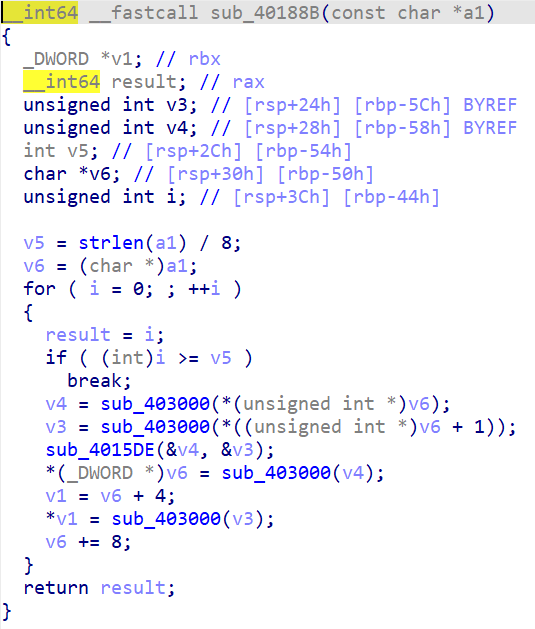
看主函数,非常简单,v7应该是key,经 sub_40188B 加密后与 Str2 比较
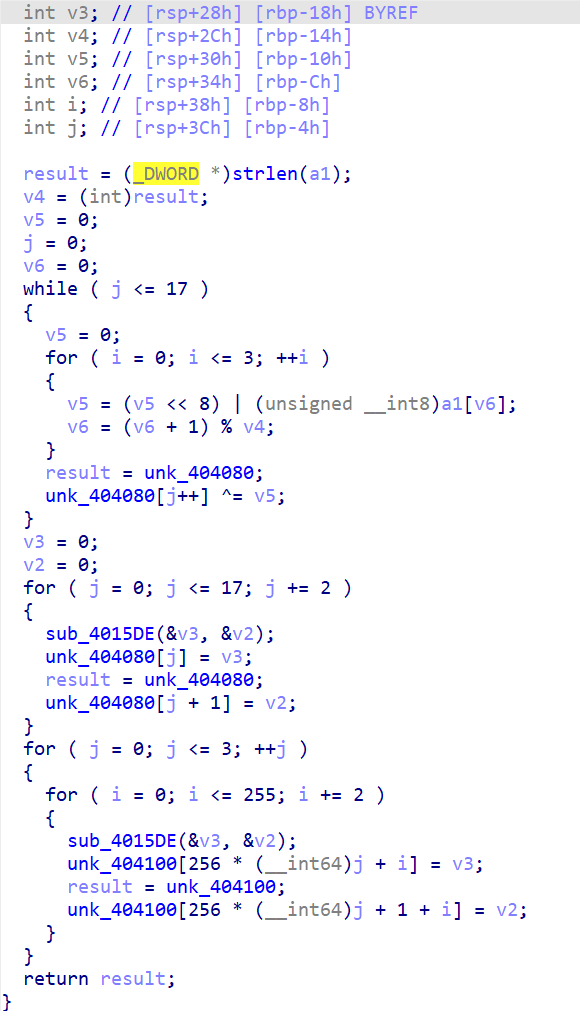
阅读一下 sub_4016C1 和 sub_40188B
应该能看出来是 Blowfish或者 Findcrypt/Signsrch 一下
解 Blowfish 就行
exp
1 | from Crypto.Cipher import Blowfish |
flag
flag{YouGotit!!Yougoit!!!!TheFifthPZGALAXYLEVEL}
easy_js2
flag为 flag{加密算法_key}
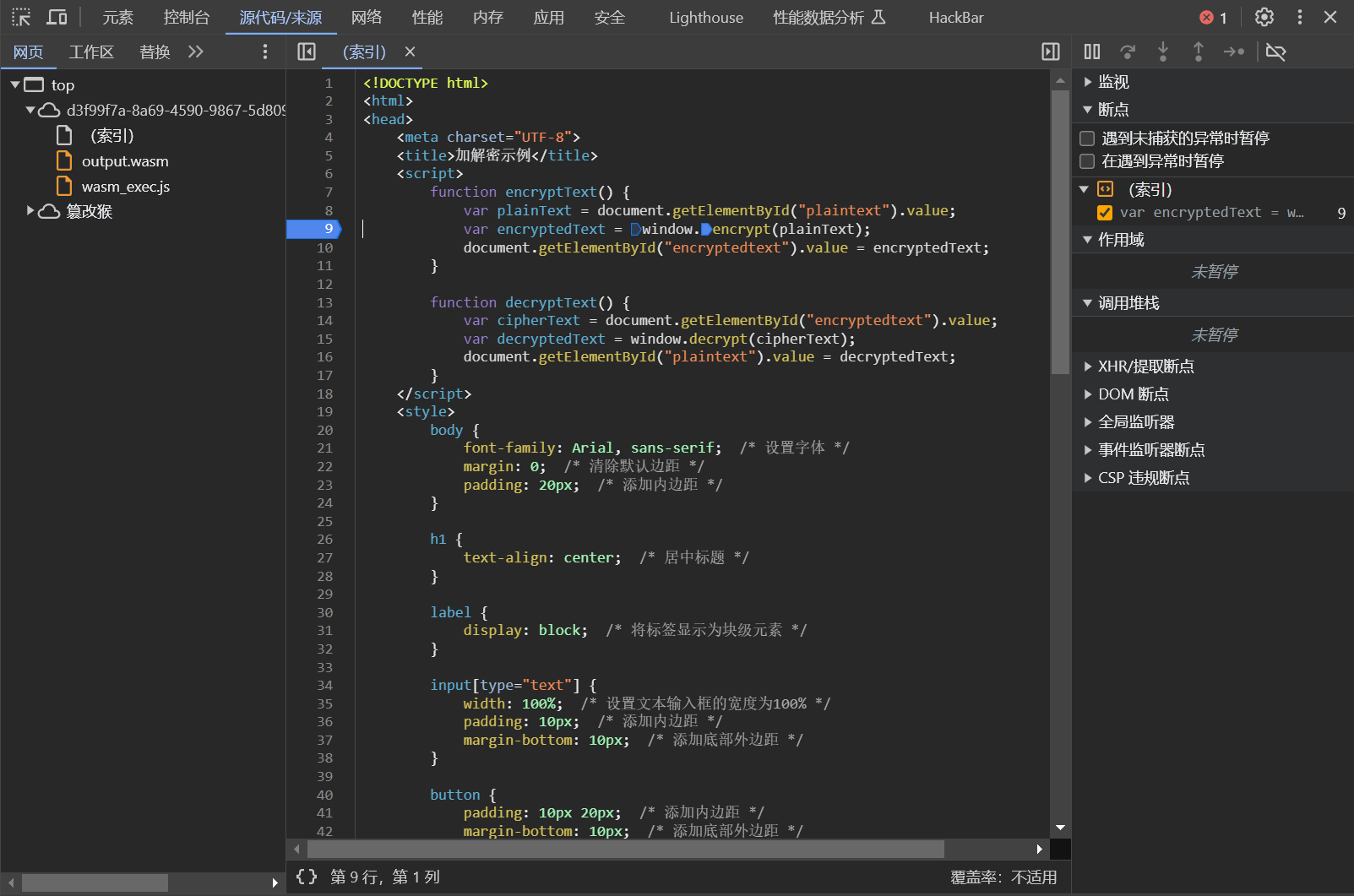
打开靶机,先看看源码
1 |
|
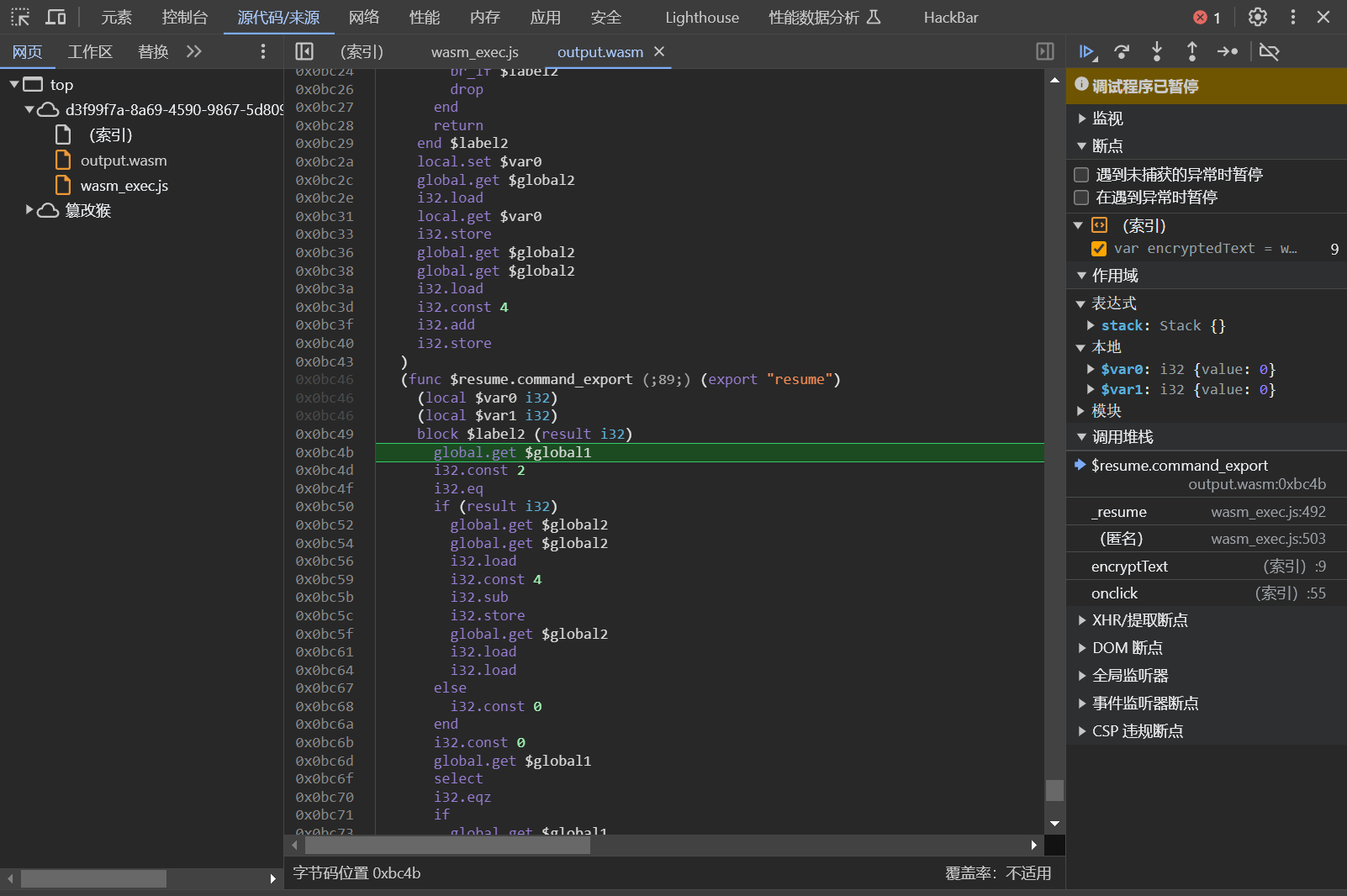
跟踪一下第九行的encrypt,加个断点
F9 后跳转到wasm_exec.js
wasm_exec.js 里没是没有用的东西,后来才知道这是生成wasm时的胶水层代码
继续F9,跳转到output.wasm
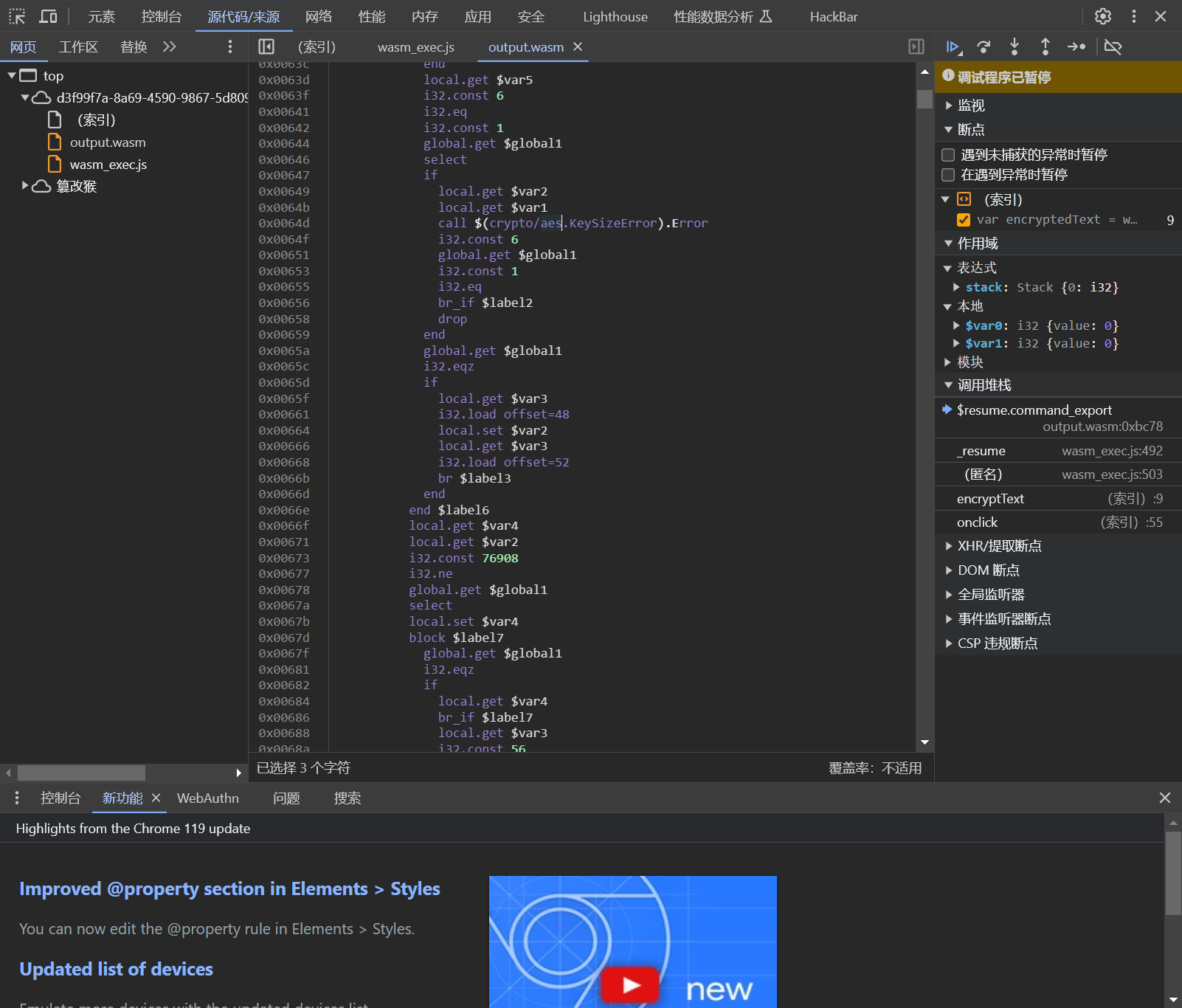
看起来有点像 python 的opcode
翻一下wasm,可以发现有aes标志,猜测是aes加密
接下来就是寻找key了
我们先了解一下wasm
搜索一下 wasm
找到了Hk_Mayfly大佬的文章Wasm逆向分析
Wasm
WebAssembly缩写为wasm,是基于堆栈的虚拟机指令集。Wasm是一种可移植、大小和加载时间效率都很好的二进制格式,可以在现代Web浏览器中运行,并且可以与JavaScript高效交互。
Wabt
Wabt是一个WebAssembly二进制工具包,包含了wasm-assembler(汇编器)、wasm-disassembler(反汇编器)、wasm-interpreter(解释器)、wasm2c(将wasm转换为C语言)、wasm-opcodecnt(统计wasm指令使用频率)、wasm-validate(验证wasm模块是否有效)等工具。
功能
- wasm-as:将wast文件转换为wasm文件
- wasm-dis:将wasm文件转换为wast文件
- wasm-interp:解释执行wasm文件
- wasm2c:将wasm文件转换为C语言文件
- wasm-opcodecnt:统计wasm文件中指令的使用频率
- wasm-validate:验证wasm文件是否有效
- wasm2wat:将wasm文件转换为wat文件
- wat2wasm:将wat文件转换为wasm文件
- wasm-objdump:反汇编wasm文件
- wasm-strip:去除wasm文件中的调试信息
- wasm-reduce:减小wasm文件的大小
- wasm-decompile:反编译wasm文件
- wasm2json:将wasm文件转换为json文件
- json2wasm:将json文件转换为wasm文件
- wasm-opcode-table:生成wasm指令表
- wasm-interp-logging:解释执行wasm文件并打印日志
安装
1 | git clone --recursive https://github.com/WebAssembly/wabt |
wasm2c
另存output.wasm到wasm2c文件夹下
1 | wasm2c -o output.c output.wasm |
目录下生成了两个文件outtput.c和output.h
此时的output.c并不直观,难以阅读,我们需要对其进行优化
将output.c,output.h和wabt/wasm2c项目内的wasm-rt.h,wasm-rt-impl.c,wasm-rt-impl.h三个文件放到同一个文件夹。
gcc编译output.c
直接gcc wasm.c会报错,因为很多wasm的函数没有具体的实现。但是我们可以只编译不链接,我们关心的只是程序本身的逻辑,不关心函数的实现。
1 | gcc -c output.c -o output.o |
output.o 用IDA打开,分析就行了
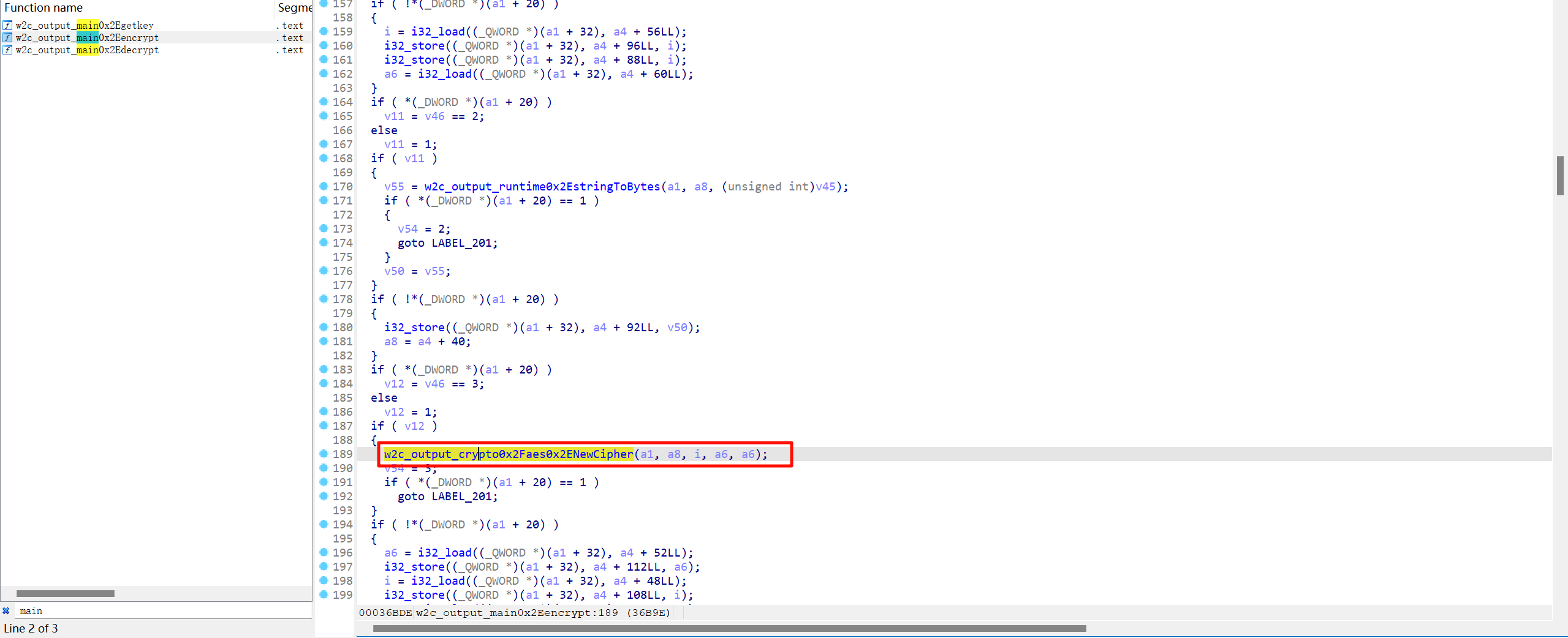
搜索main,在w2c_output_main0x2Eencrypt函数里可以看到调用了
w2c_output_crypto0x2Faes0x2ENewCipher
再跟踪一下参数就能找到key了newstarTrealstar
flag
flag{aes_newstarTrealstar}
TheLastDance
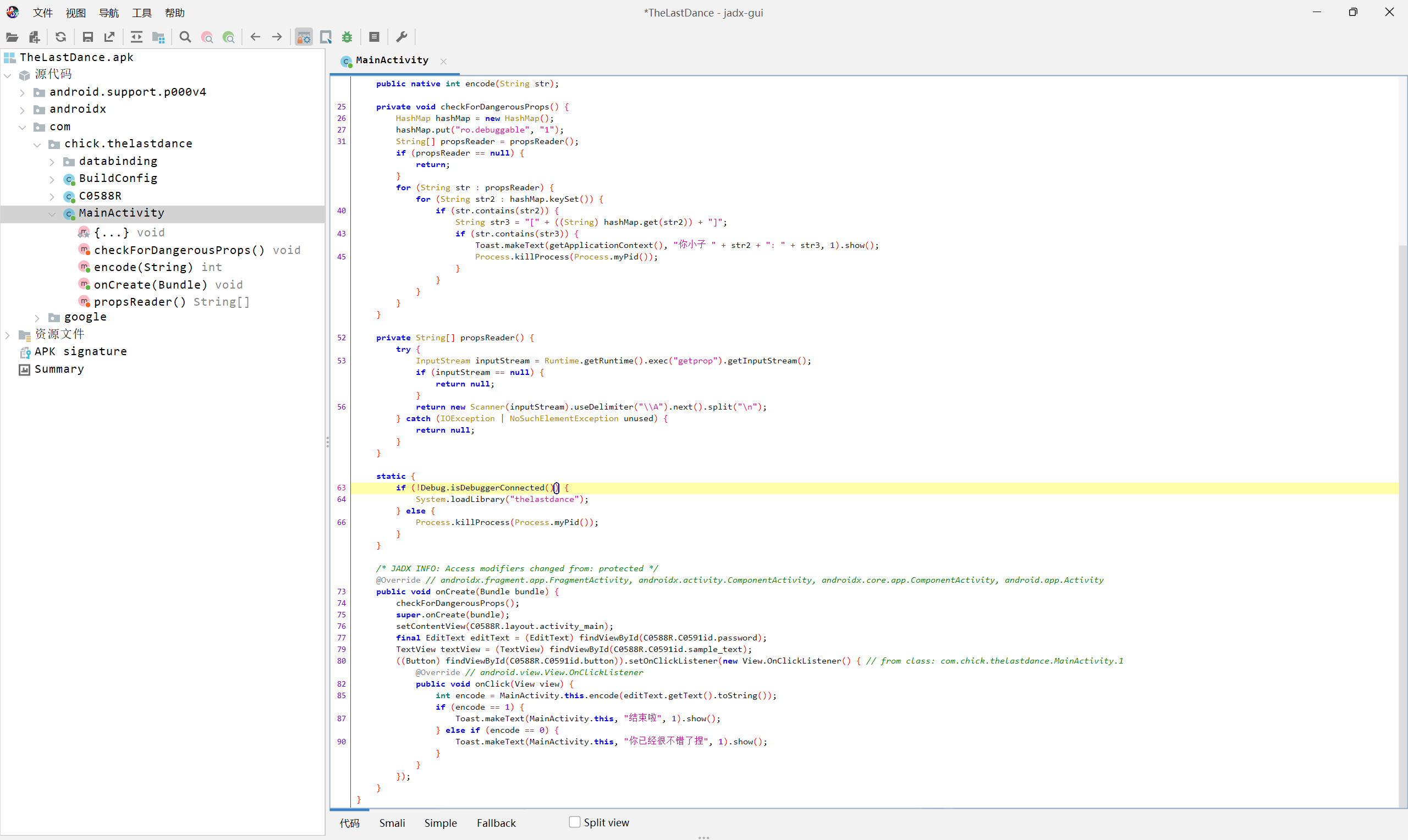
先看看java层的mainactivity
没有加密逻辑,只有反调试,
检测到没有调试后会调用native层的thelastdance来进行encode
看看so文件
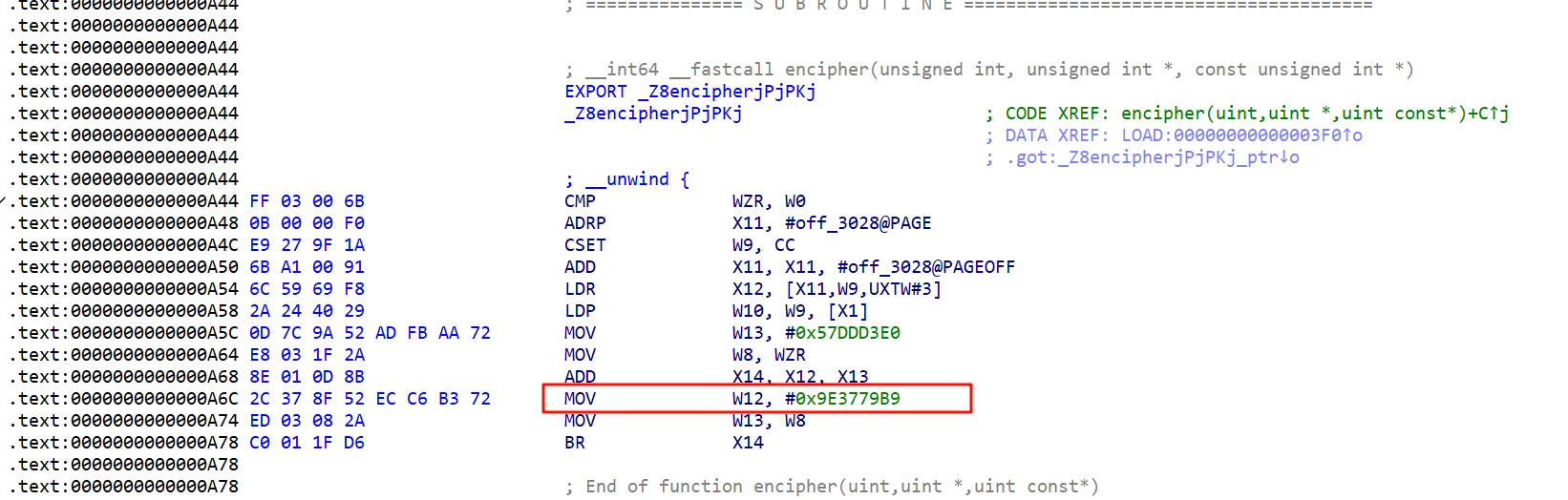
找到encipher函数
看到0x9E3779B9,应该是XTEA加密
找一下密文和key
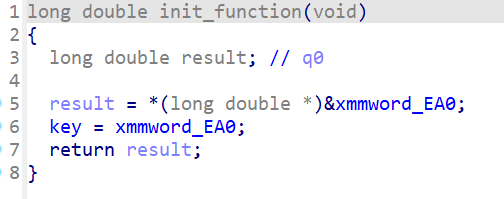
init_function对key进行了修改
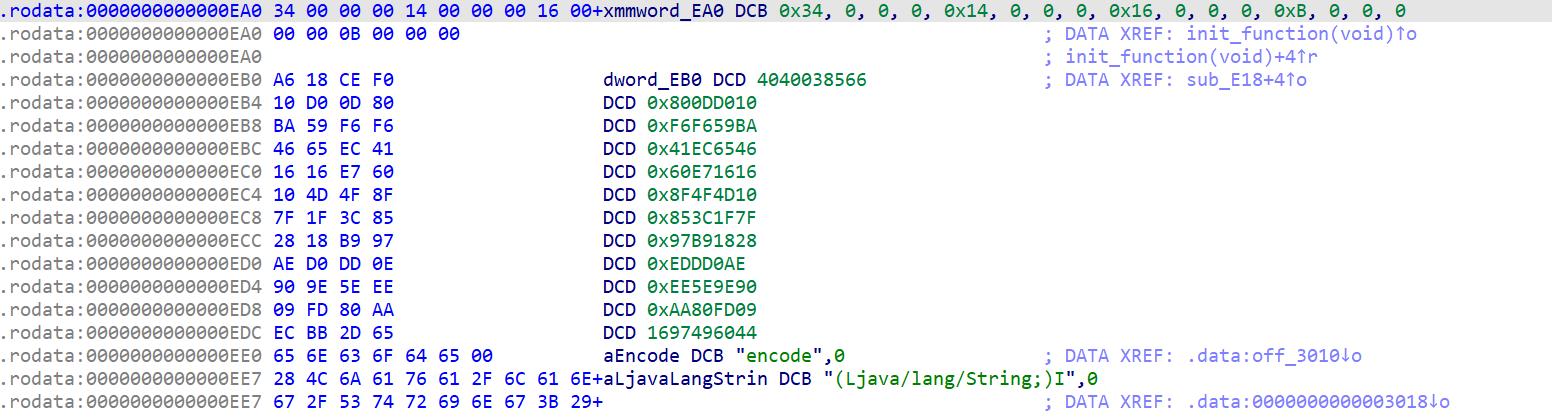
跟踪一下xmmword_EA0
看到密文和key
exp
1 |
|
flag
flag{K1k1_S_1ov3_fr0m_Ch1ck_wh0_1s_w0rk1ng_h@rD}