强网杯2023
强网先锋
babyre
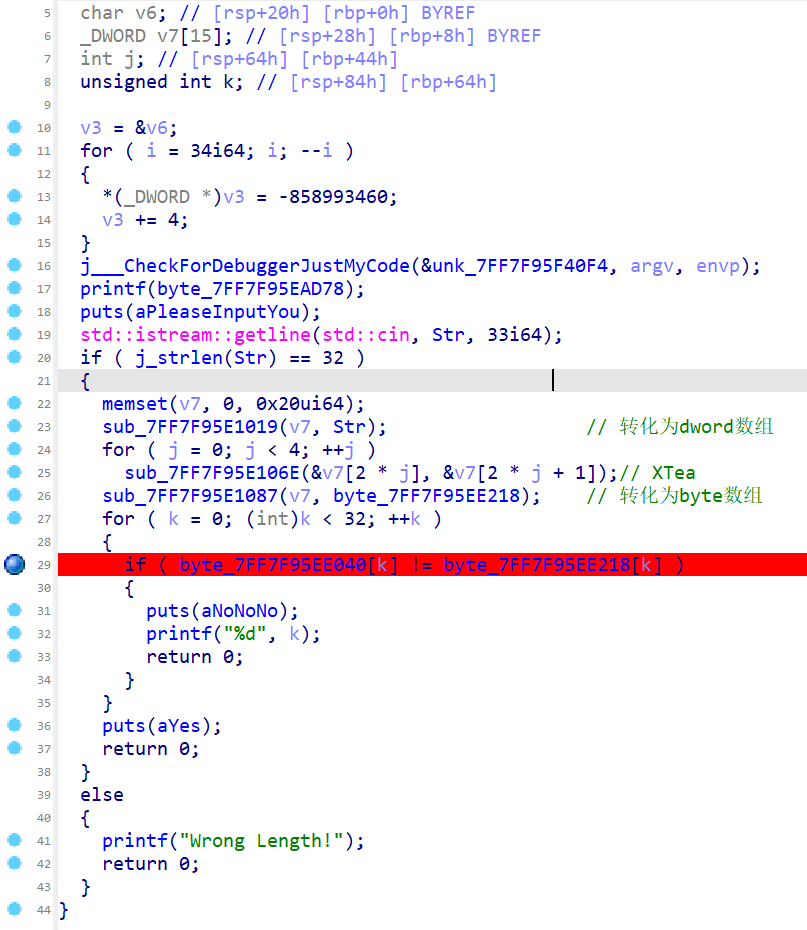
主函数分析如下
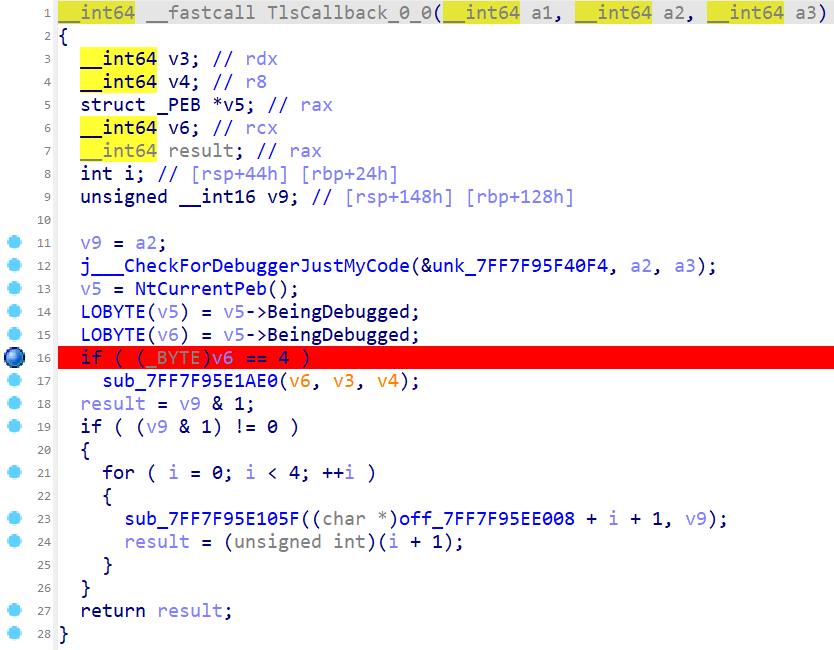
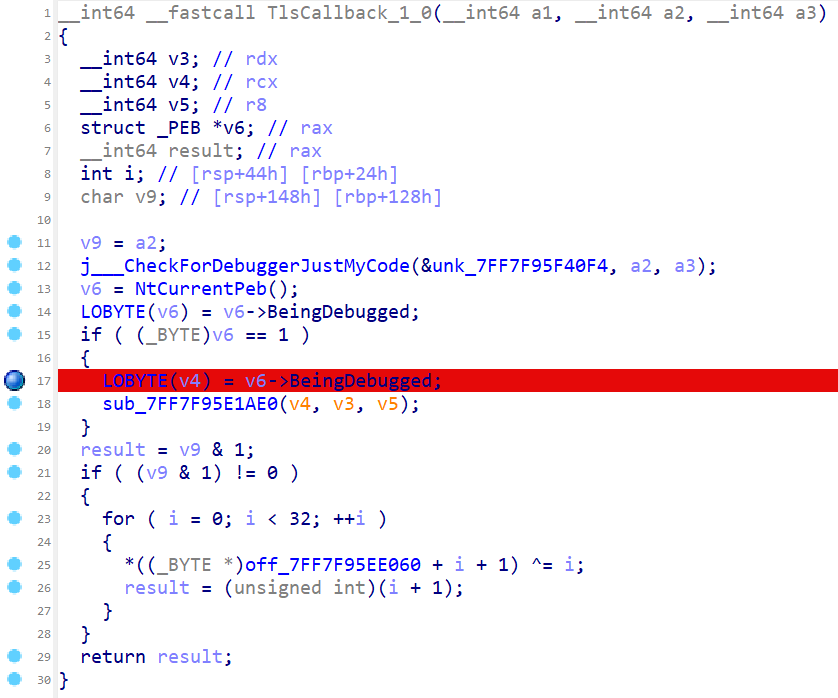
同时注意到有 TLS 反调试
TLS反调试里修改了数据,考虑动调获取数据
先绕过两个 BeingDebugged
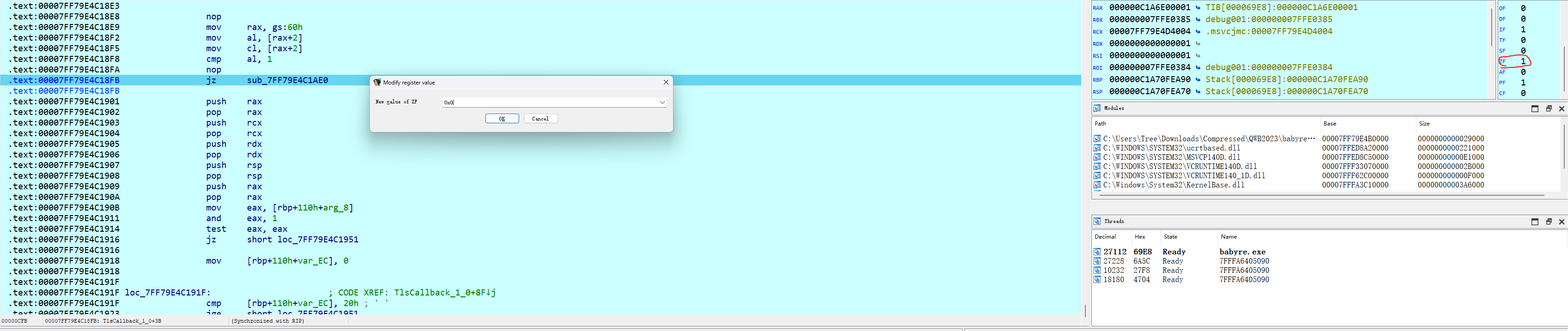
运行到 jz 跳转指令处,修改 ZF 标志为 0
下一个 jz 跳转指令处,修改 ZF 标志为 0
此时再 F9 运行,提示进到主函数里
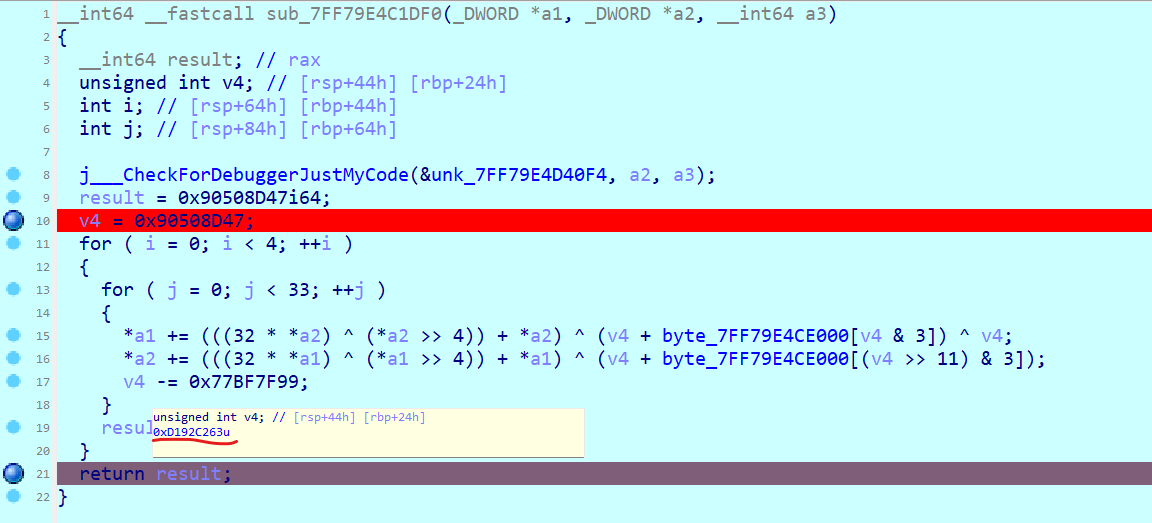
随便输入长度为32的字符串,此时 IDA 进入了 TEA 函数
TEA 函数 IDA 分析有点问题
看看汇编
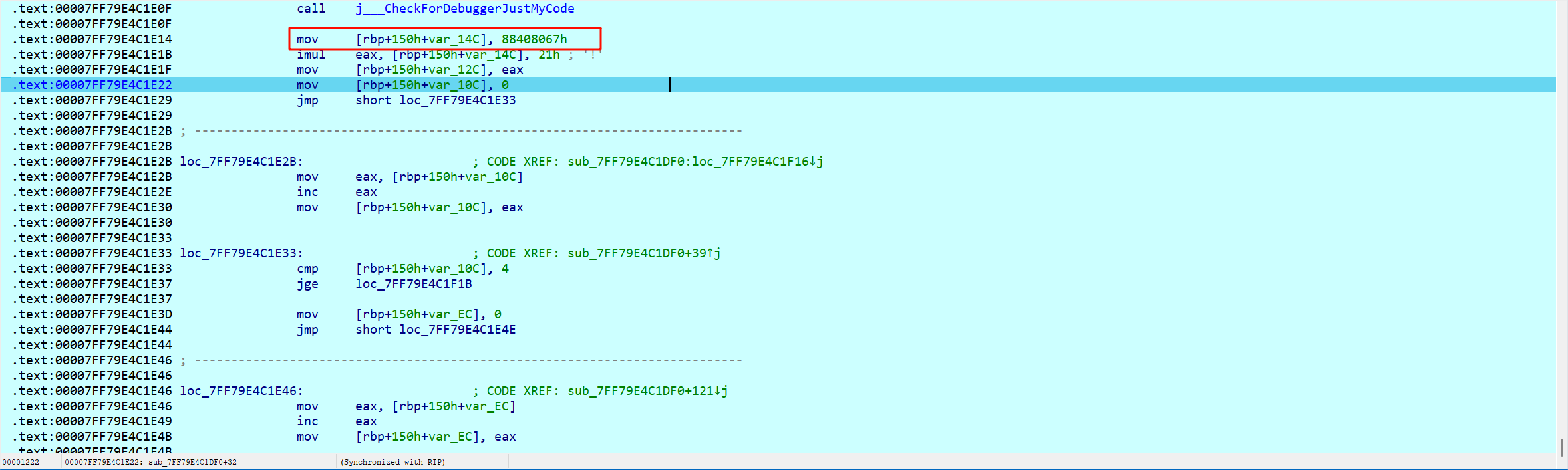
可以看到实际的 delta 值为 0x88408067
我们可以通过计算获取到解密脚本需要的 sum 值
也可以顺手在该函数中获取一下,运行第二个断点 return 处
查看一下 v4 的值 0xD192C263
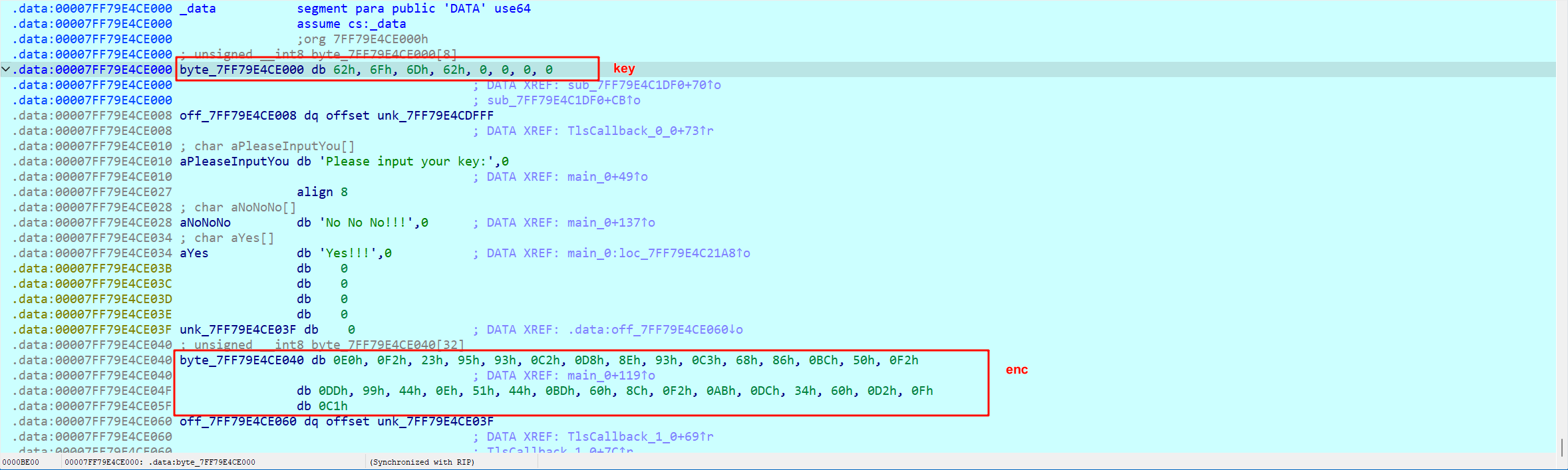
最后回到主函数获取一下经过修改的 key 和 enc
exp
1 |
|
flag
flag{K1k1_S_1ov3_fr0m_Ch1ck_wh0_1s_w0rk1ng_h@rD}
ezre
OLLVM 混淆控制流平坦化 D810 梭
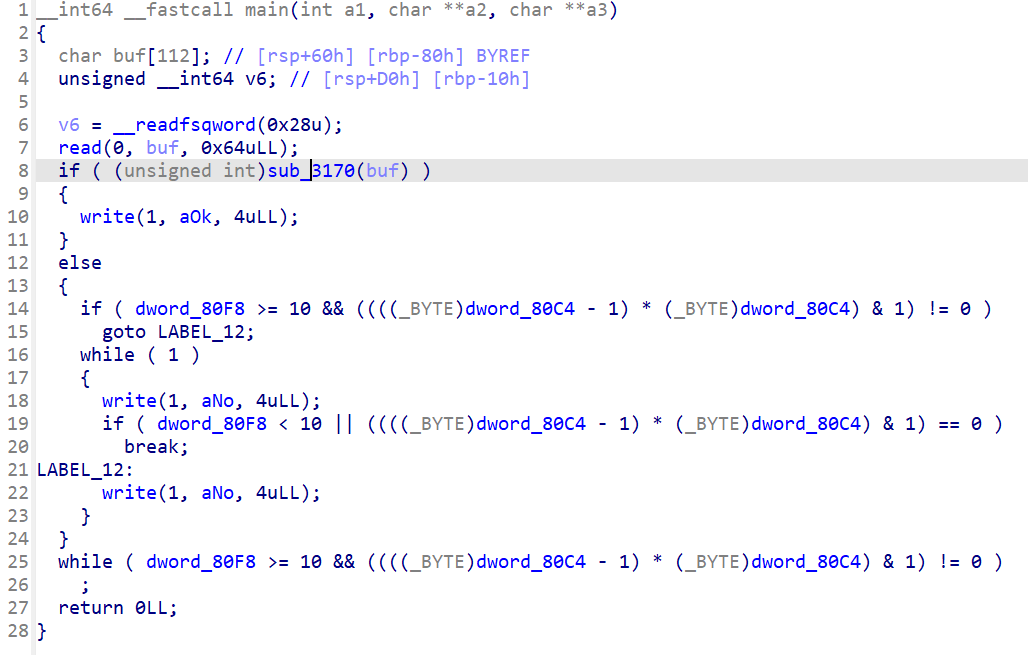
主函数如下
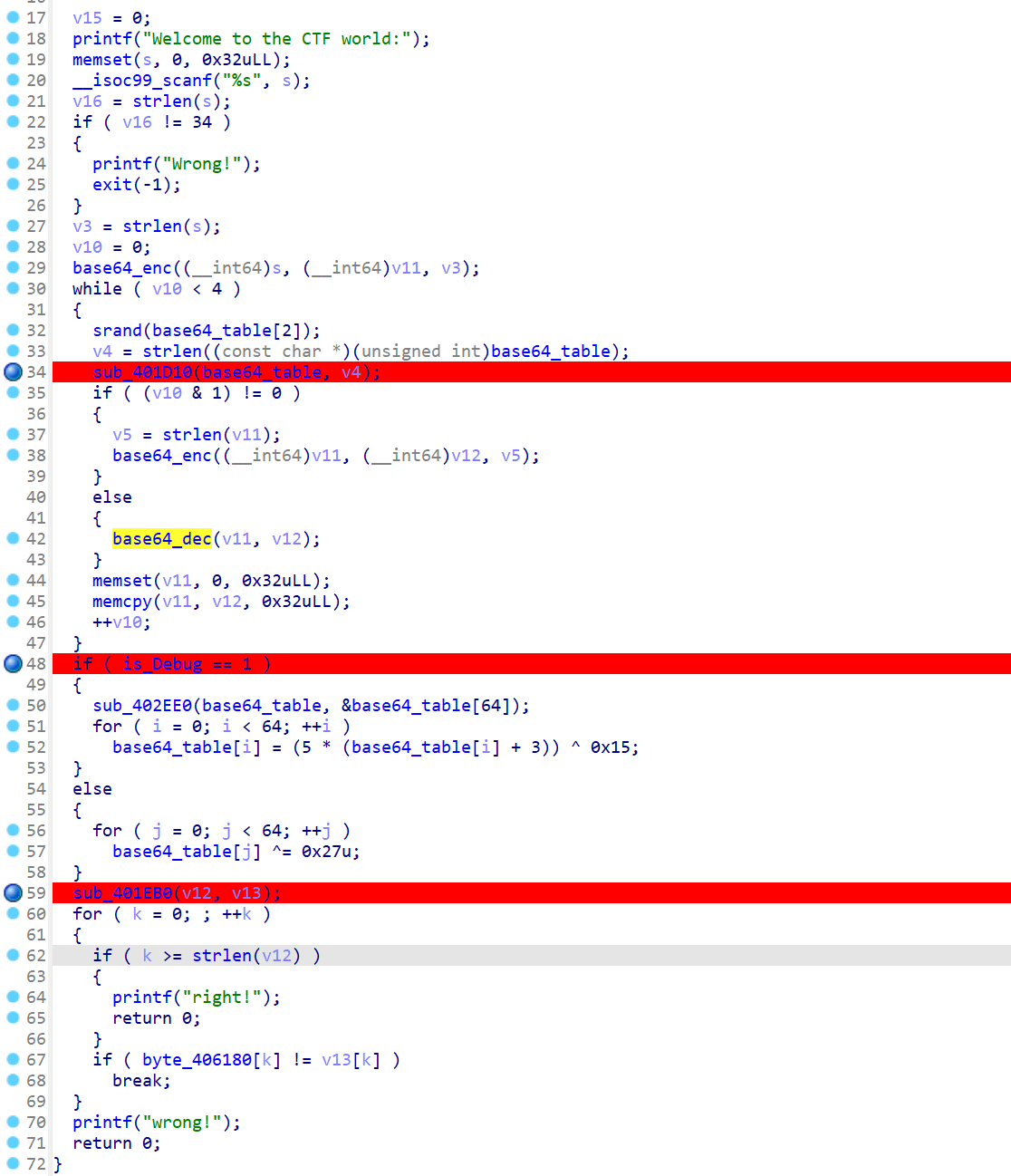
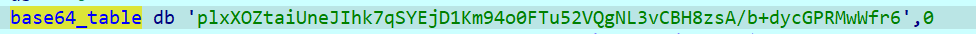
先看最后一步 sub_401EB0
先逆一下,动调取出 base64_Table
1 | enc =[0x3A, 0x2C, 0x4B, 0x51, 0x68, 0x46, 0x59, 0x63, 0x24, 0x04, 0x5E, 0x5F, 0x00, 0x0C, 0x2B, 0x03, 0x29, 0x5C, 0x74, 0x70, 0x6A, 0x62, 0x7F, 0x3D, 0x2C, 0x4E, 0x6F, 0x13, 0x06, 0x0D, 0x06, 0x0C, 0x4D, 0x56, 0x0F, 0x28, 0x4D, 0x51, 0x76, 0x70, 0x2B, 0x05, 0x51, 0x68, 0x48, 0x55, 0x24, 0x19] |
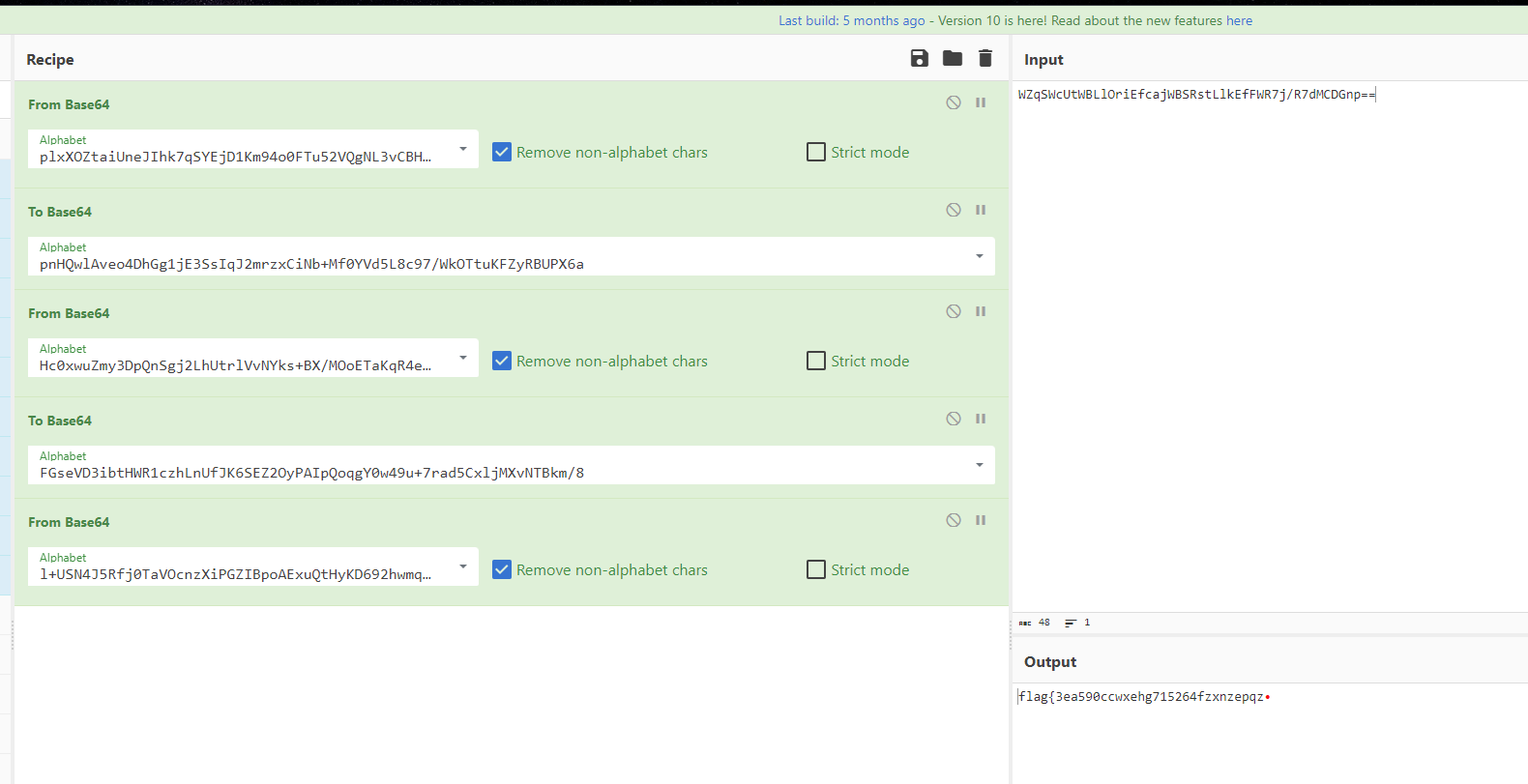
最后再返回去依次用
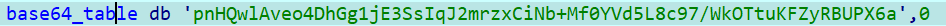
plxXOZtaiUneJIhk7qSYEjD1Km94o0FTu52VQgNL3vCBH8zsA/b+dycGPRMwWfr6解码
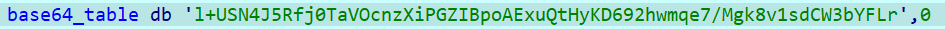
pnHQwlAveo4DhGg1jE3SsIqJ2mrzxCiNb+Mf0YVd5L8c97/WkOTtuKFZyRBUPX6a编码
Hc0xwuZmy3DpQnSgj2LhUtrlVvNYks+BX/MOoETaKqR4eb9WF8ICGzf6id1P75JA解码
FGseVD3ibtHWR1czhLnUfJK6SEZ2OyPAIpQoqgY0w49u+7rad5CxljMXvNTBkm/8编码
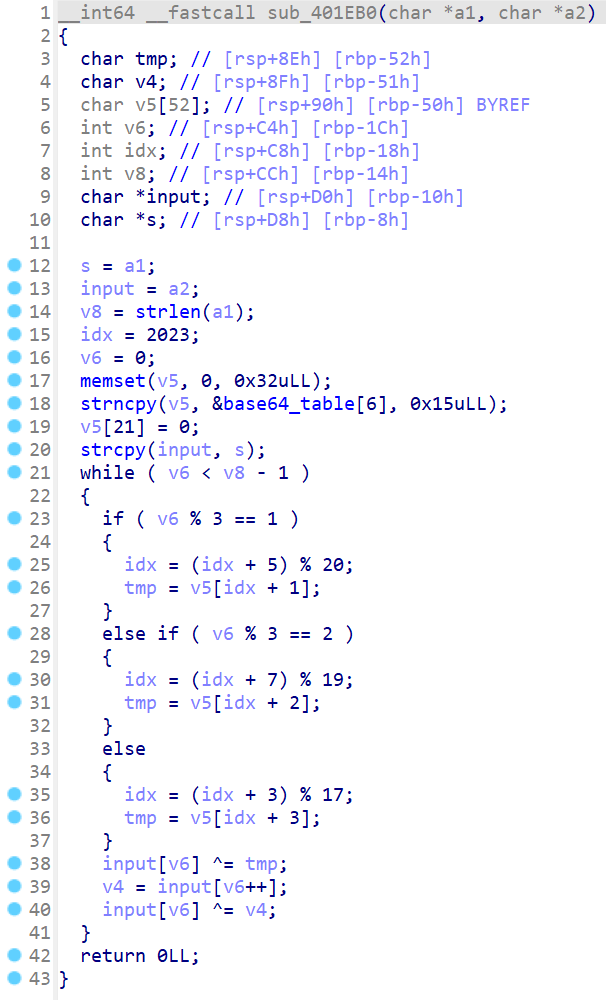
l+USN4J5Rfj0TaVOcnzXiPGZIBpoAExuQtHyKD692hwmqe7/Mgk8v1sdCW3bYFLr解码
exp
1 | import base64 |
flag
flag{3ea590ccwxehg715264fzxnzepqz}
Reverse
ezre
同样的 OLLVM 混淆控制流平坦化 D810 梭
主函数如下
没什么有价值信息,只在 sub_3180 里看到了假 flag
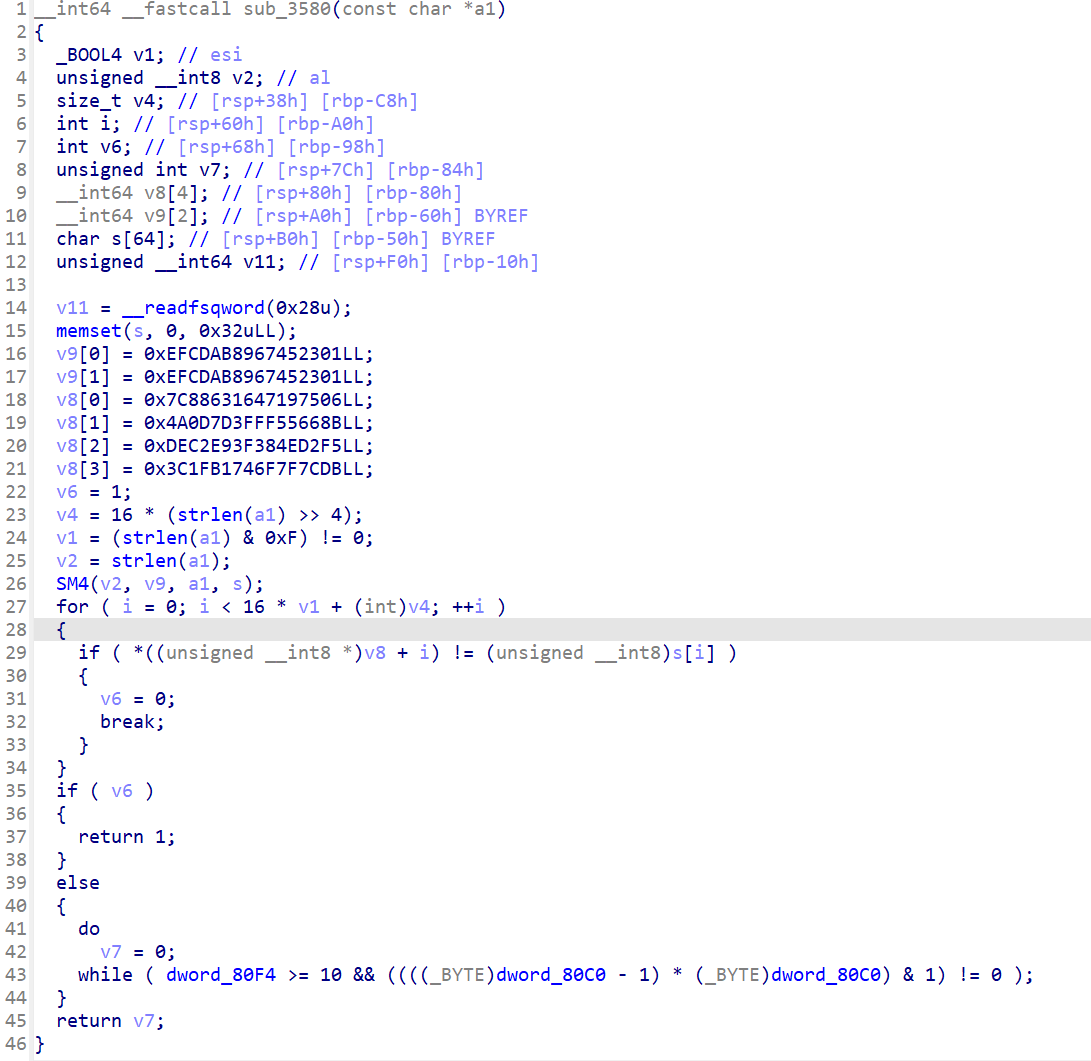
函数不多一个个找,发现 sub_3580 里有个可疑数据,长得很像加密过程
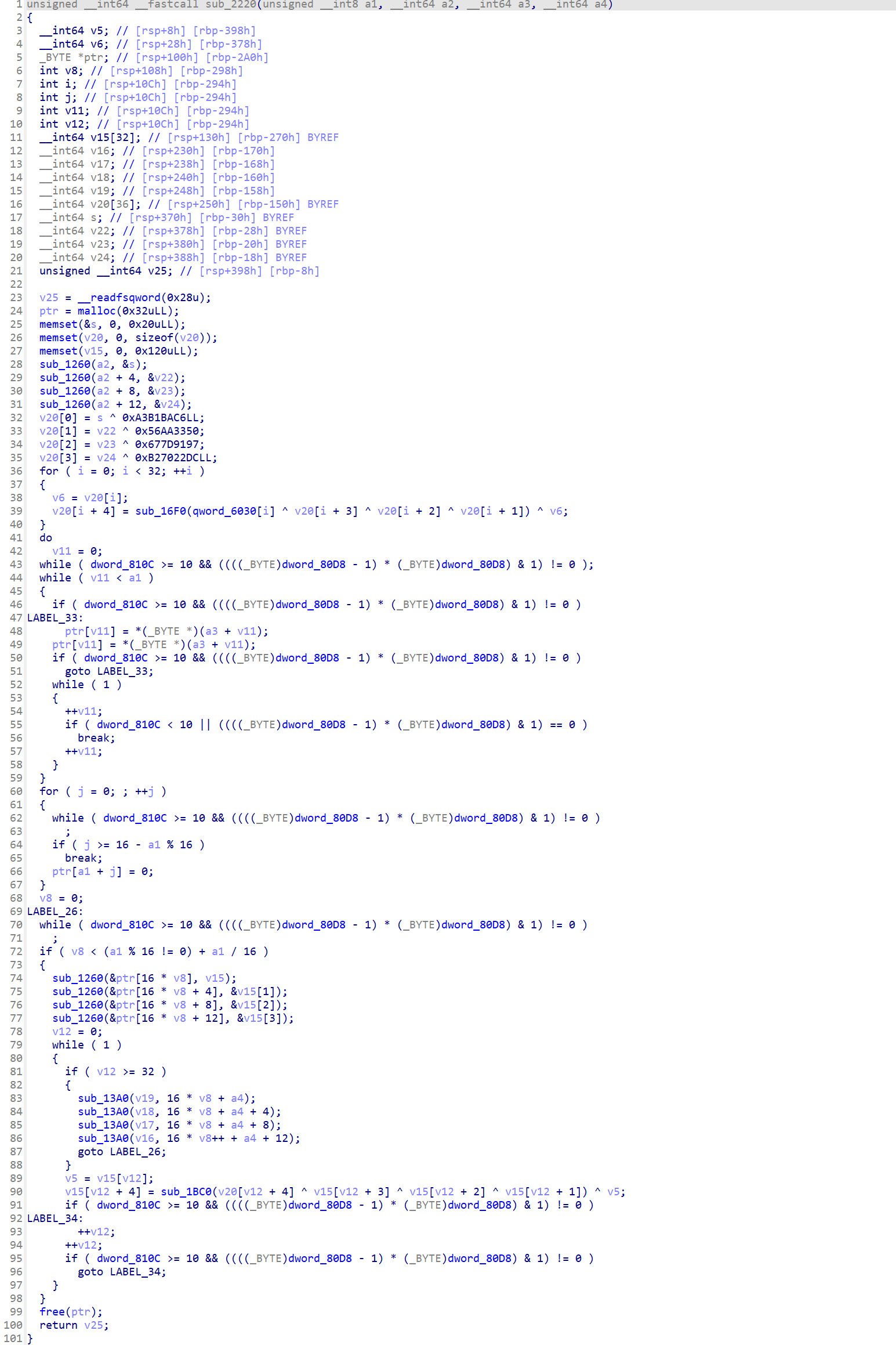
而且调用了 sub_2220 可以看出来是 SM4 加密 signsrch 也识别出来了
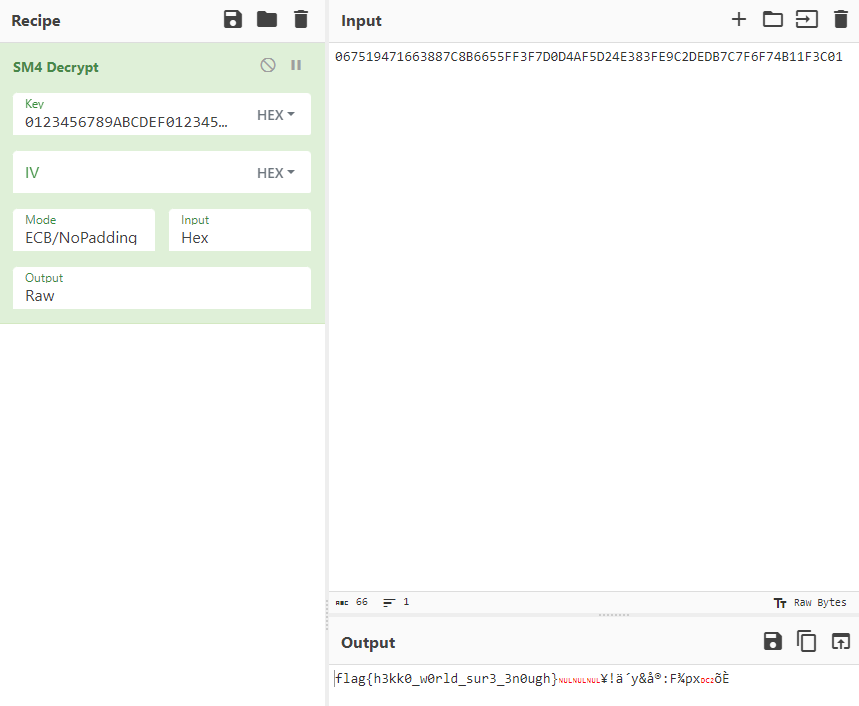
直接 cyberchef 梭
flag
flag{h3kk0_w0rld_sur3_3n0ugh}
dotdot
DIE 查看 PE 结构发现是 .NET 程序
用 dnSpy 打开,发现有数据没有反编译出来
改用 ILSpy 打开,正常反编译可以看到数据
AAA 是白盒 AES
BBB 是长度判断,要求长度为16
CCC 是比较函数,
DDD 是 License.dat 的读取函数
EEE 是将输入作为 key 进行 RC4 解密 License.dat
FFF 里进行 TEA 加密,然后校验加密结果,并且对 License.dat 进行MD5校验,校验正确了再异或求出正确flag
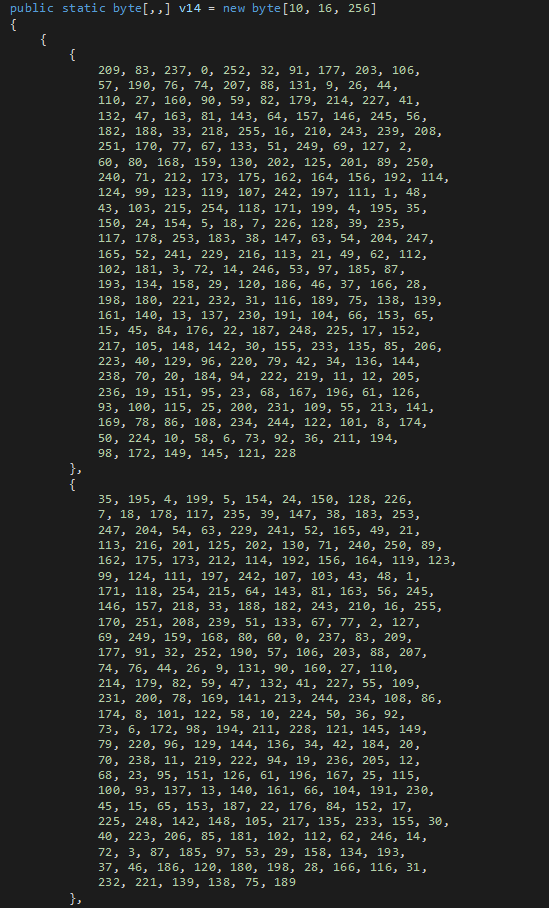
一步步来,先解白盒 AES 可以看到 v14 是 Tboxes
whitebox-aes
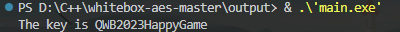
解出来主密钥为 QWB2023HappyGame
AES 解密一下 v4 解出 RC4 的 key 也就是输入
1 | from Crypto.Cipher import AES |
然后 RC4 解密 License.dat
1 | from Crypto.Cipher import ARC4 |
接着随便写个 C# 读取 License_decry.dat
1 | using System; |
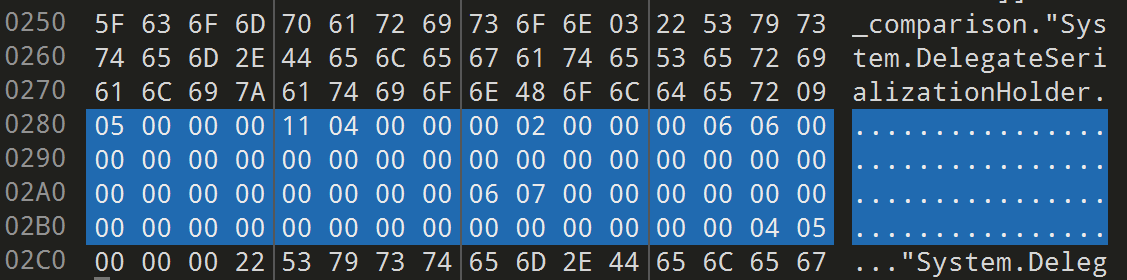
发现报错,应该是需要修复
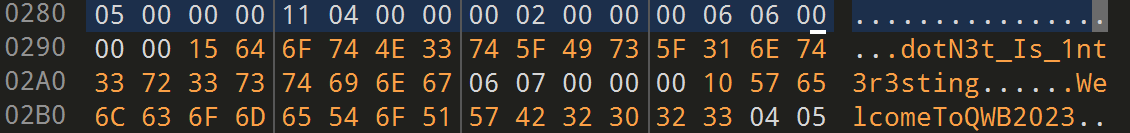
这一段数据前一段0字节长度为0x15,后一段长度为0x10
应该是 TEA 加密的数据,长度为0x15的数据是 enc,长度为0x10的数据是 key
根据 FFF 函数解一下 TEA
1 | import struct |
填入 License_decry.dat 修复一下
0x15和0x10是长度
最后由 MD5 求出 flag
1 | # 将缺失的数据填入 License_decry.dat |
exp
1 | from Crypto.Cipher import AES |
flag
flag{d0tN3t_I5_Ea57_2_y09!G00d_Luck}
unname
java 层面的反调试,用 jadx 打开,没发现什么逻辑,
只能看到调用了 native 层的 check 函数
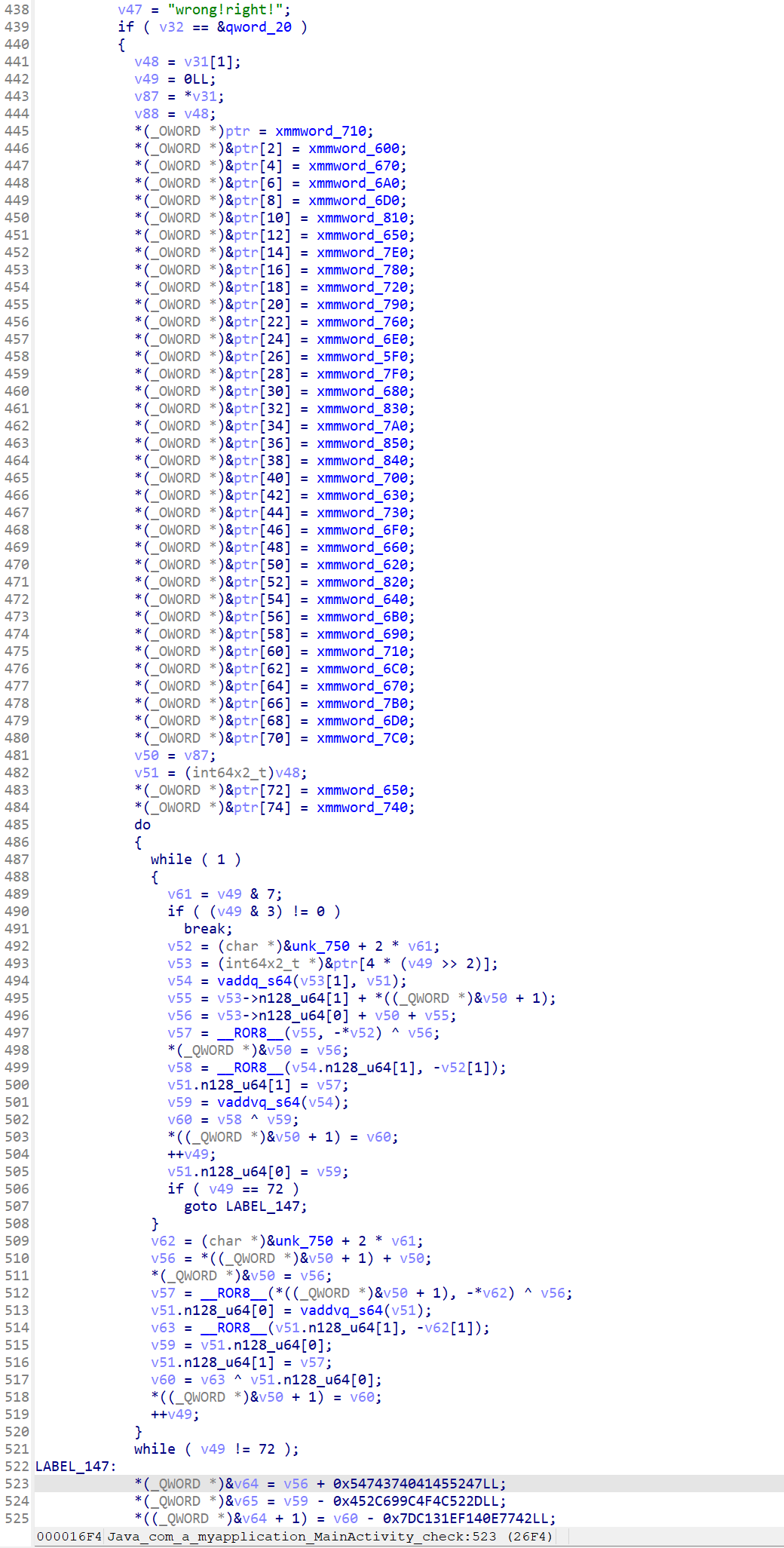
so 文件里 check 函数挺长的,调试一下
找到关键运算
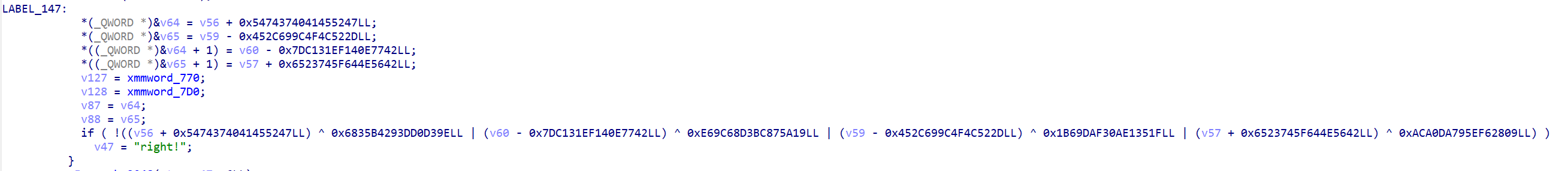
label_147 是最终的判断
计算一下
1 | from z3 import * |
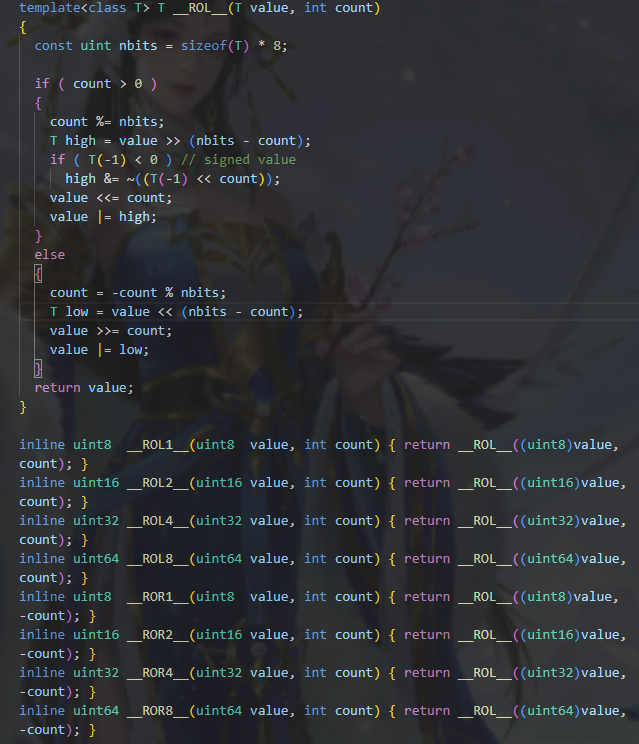
通过 ida/plugins/defs.h 查看__ROR8__定义
即
1 | unsigned long long __ROR8__(unsigned long long val, unsigned int shift){ |
模拟while循环的加密过程
1 |
|
逆一下
exp
1 |
|
flag
flag{7hIs_I$_nEw_Try1N9_@cu7U@1}