羊城杯2024
Reverse
sedRust_happyVm
比赛没做出来,贴几个wp,复现了再说
羊城杯 · 2024 WriteUp-WgpSec狼组安全团队
2024羊城杯sedRust_happyVm
再贴个exp
1 | from base64 import * |
pic
有个图片附件,010 editor打开是乱码,被修改过了
再看可执行文件,是个GO
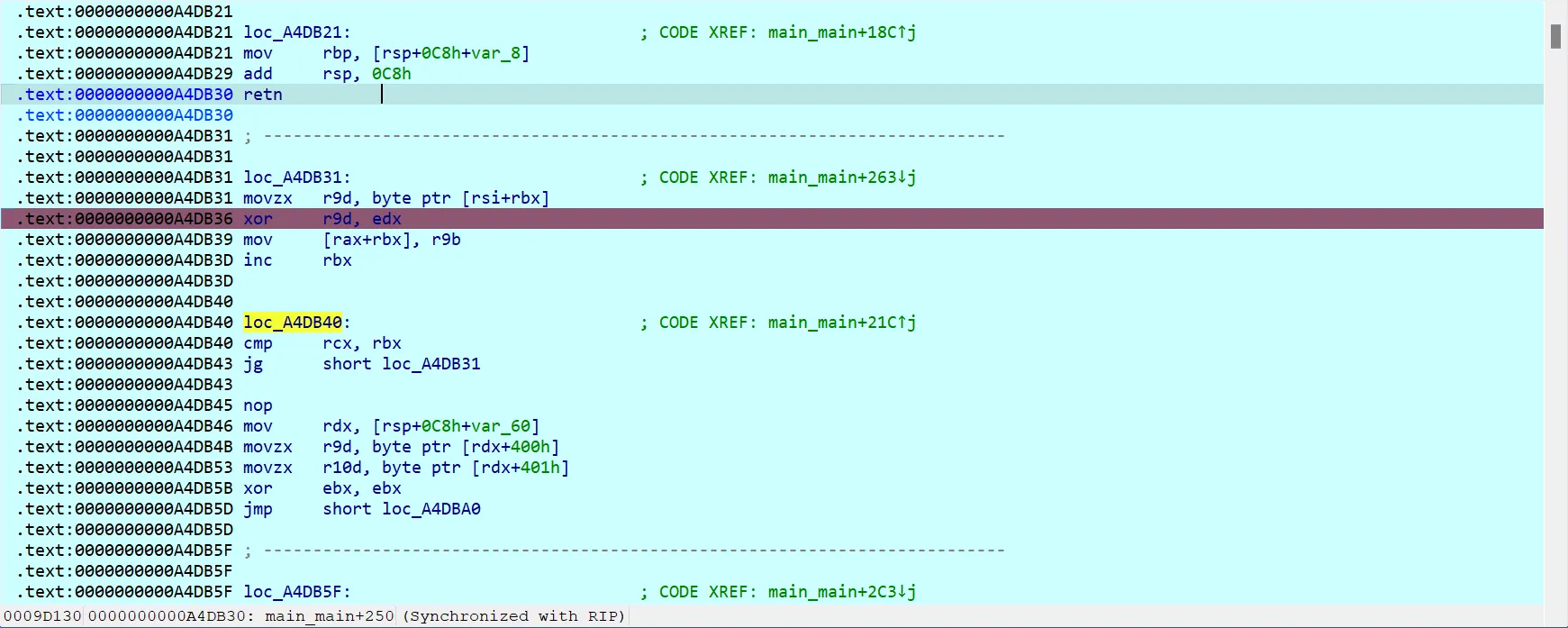
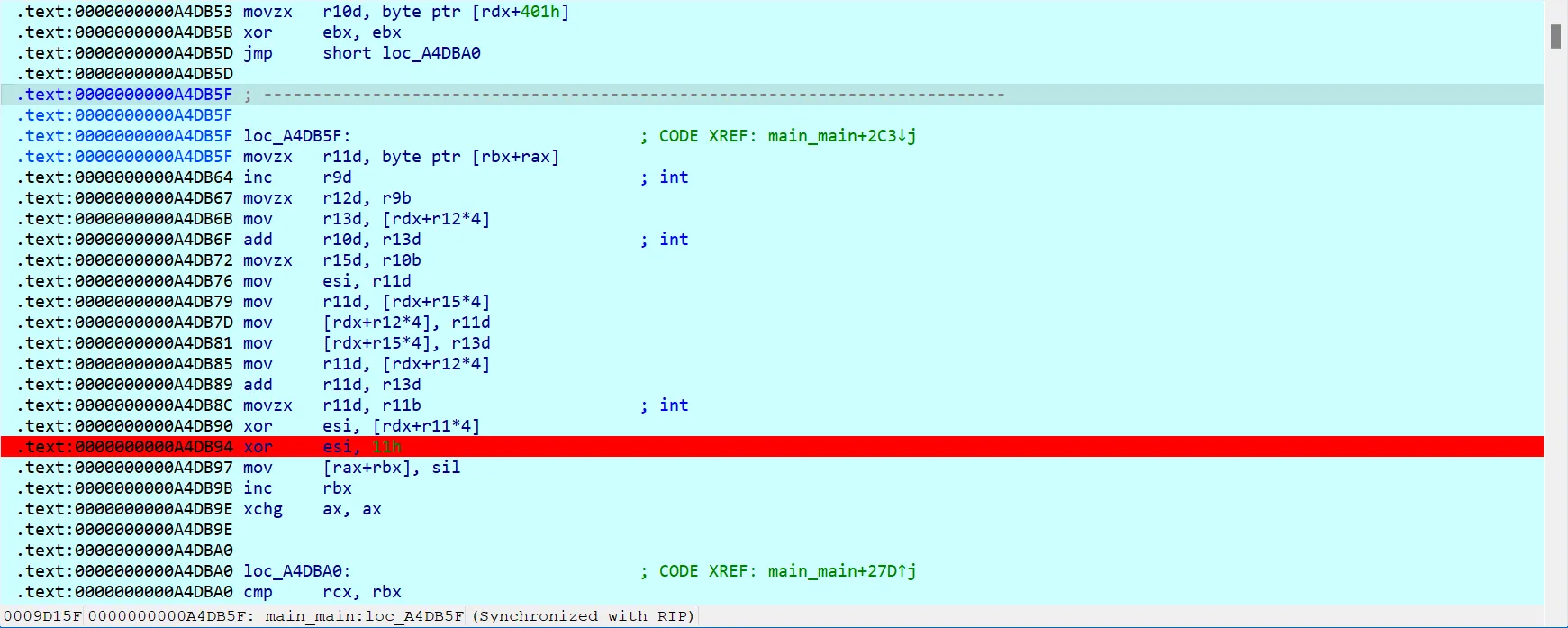
看看汇编,有个反调试简单修改ZF标志绕过一下,
要求输入key,长度为5
加密应该是个 rc4
最后异或一下key[1]和0x11就行,我们直接爆破5位key
1 | import itertools |
最后运行一下可执行文件,还原出png
DASCTF{good_y0u_get_the_ffffflag!}
docCrack
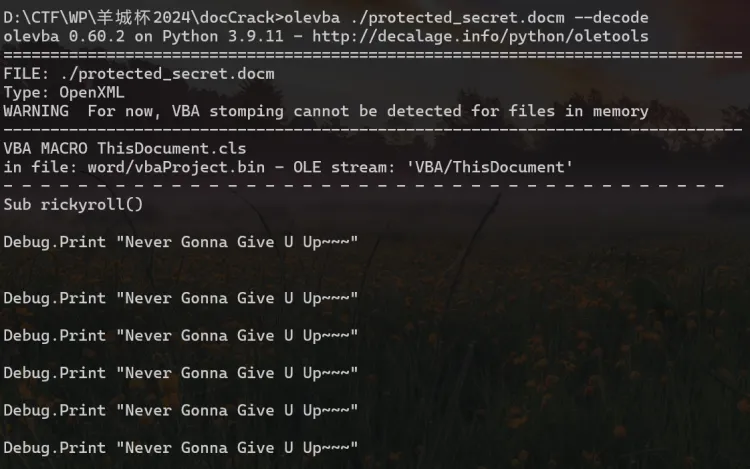
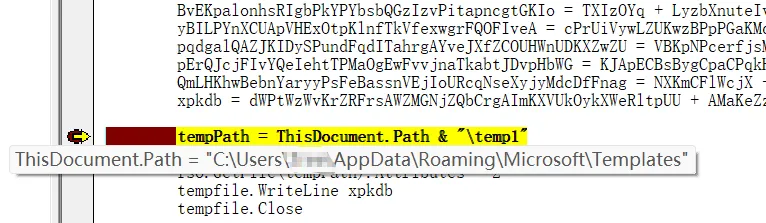
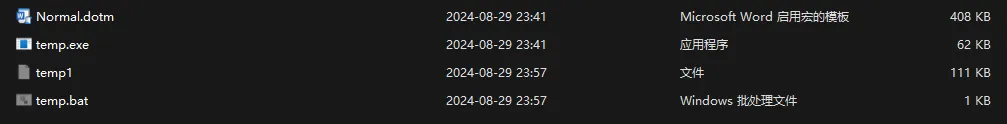
宏病毒,微步沙箱启动,拿到宏代码和释放的temp.exe(或者用olevba)
1 | pip install oletools |
看看宏代码关键的几处,这里当时没注意到异或了7
flag就是使temp.exe输出good的参数
可以尝试删除1173行,用修改过的宏代码获取temp.exe
新建一个文档,alt+F11把宏代码粘贴进去
调试获取到文件生成的位置
拿到文件
这里偷懒直接从微步拿到temp.exe
看看temp.exe
简单逆一下,但是不对得到CFTDSA|QefX6tXcfibuhrt&&&XE6pfubX7aXJfdu7XQ6ur2bt&&&z`
cyberchef魔棒启动
1 | #import Z3 |
DASCTF{Vba_1s_dangerous!!!_B1ware_0f_Macr0_V1ru5es!!!}
你这主函数保真么
主函数没有东西,但是看到了一个encrypt函数
一路交叉应用
先看看密文
check明显是类型分析错误了
全选之后按*转换成数组
看看ROT13和离散余弦变换
都没有魔改
直接np库一把梭了
1 | import numpy as np |
DASCTF{Wh0_1s_Ma1n_@nd_FunnY_Dct}
评论
TwikooWaline