TAMUCTF2024
Reverse
Official WP
Reveille Petter
这是一个用Godot引擎写的游戏,用gdsdecomp可以进行反编译
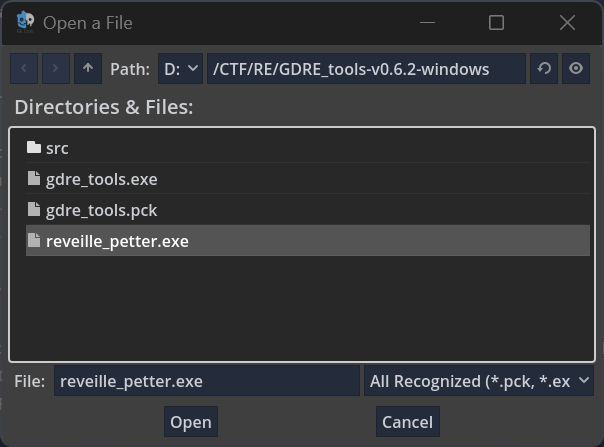
RE Tools - Recover Project 选择 reveille_petter.exe 进行反编译
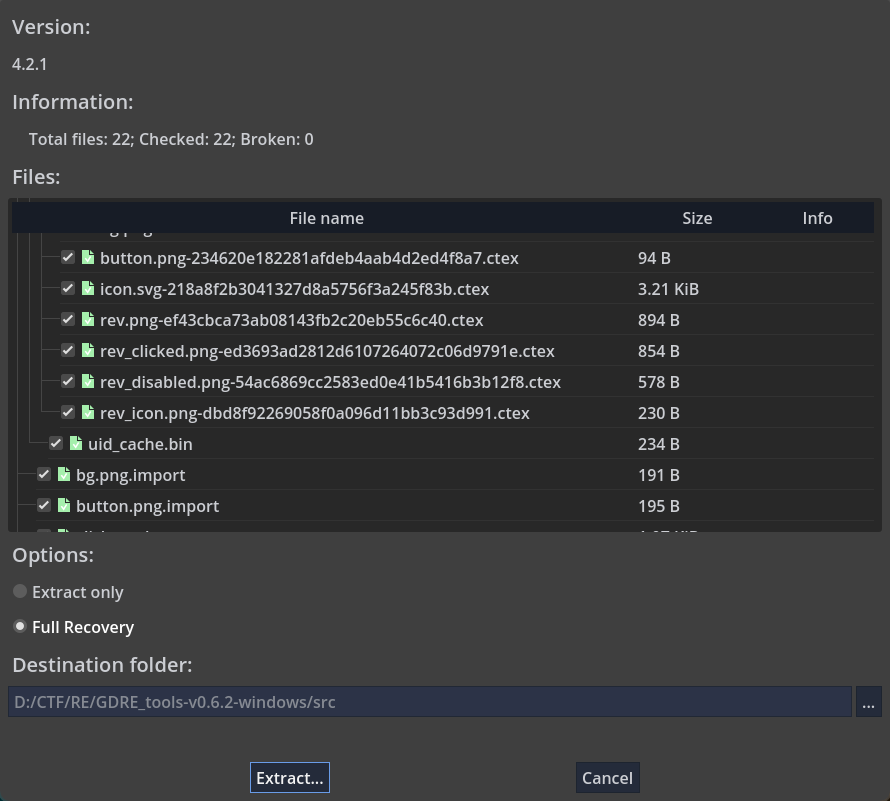
选择输出目录
在输出目录中有一个project.godot文件,可以用Godot打开
但这题用不到,重点是clicker.gd文件
这是Godot的脚本文件,在脚本文件里可以直接看到明文flag
1 | extends Node2D |
flag
gigem{r3v_1s_cut3!!}
Resistant
描述:
All these RE challenges are just too easy! So what happens when the binary fights back?
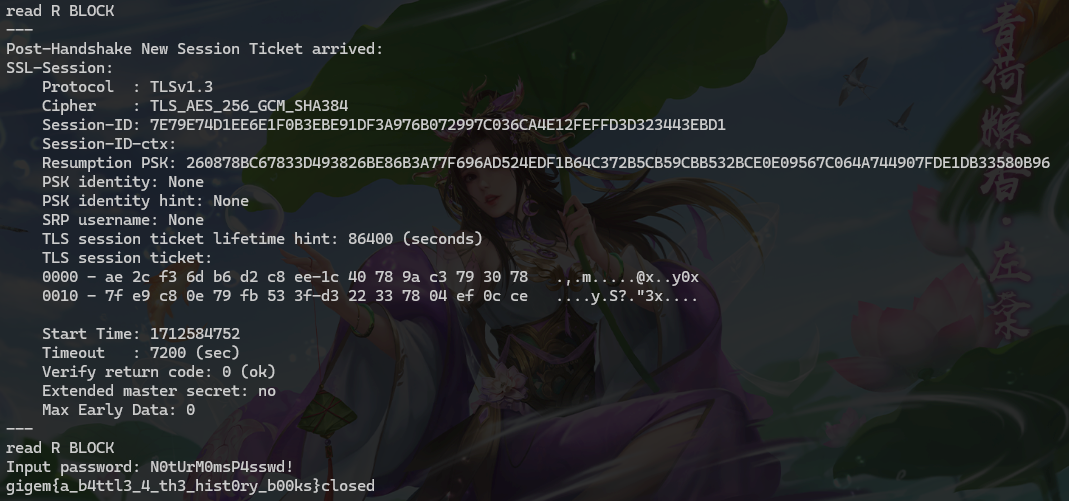
openssl s_client -connect tamuctf.com:443 -servername resistant
openssl 连接后要求我们输入密码
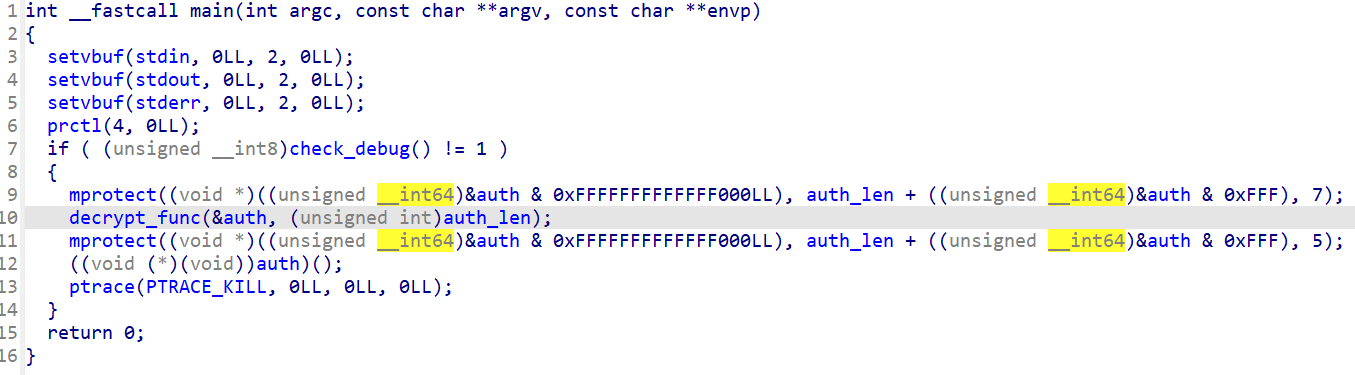
用 IDA 打开 resistant 查看main函数
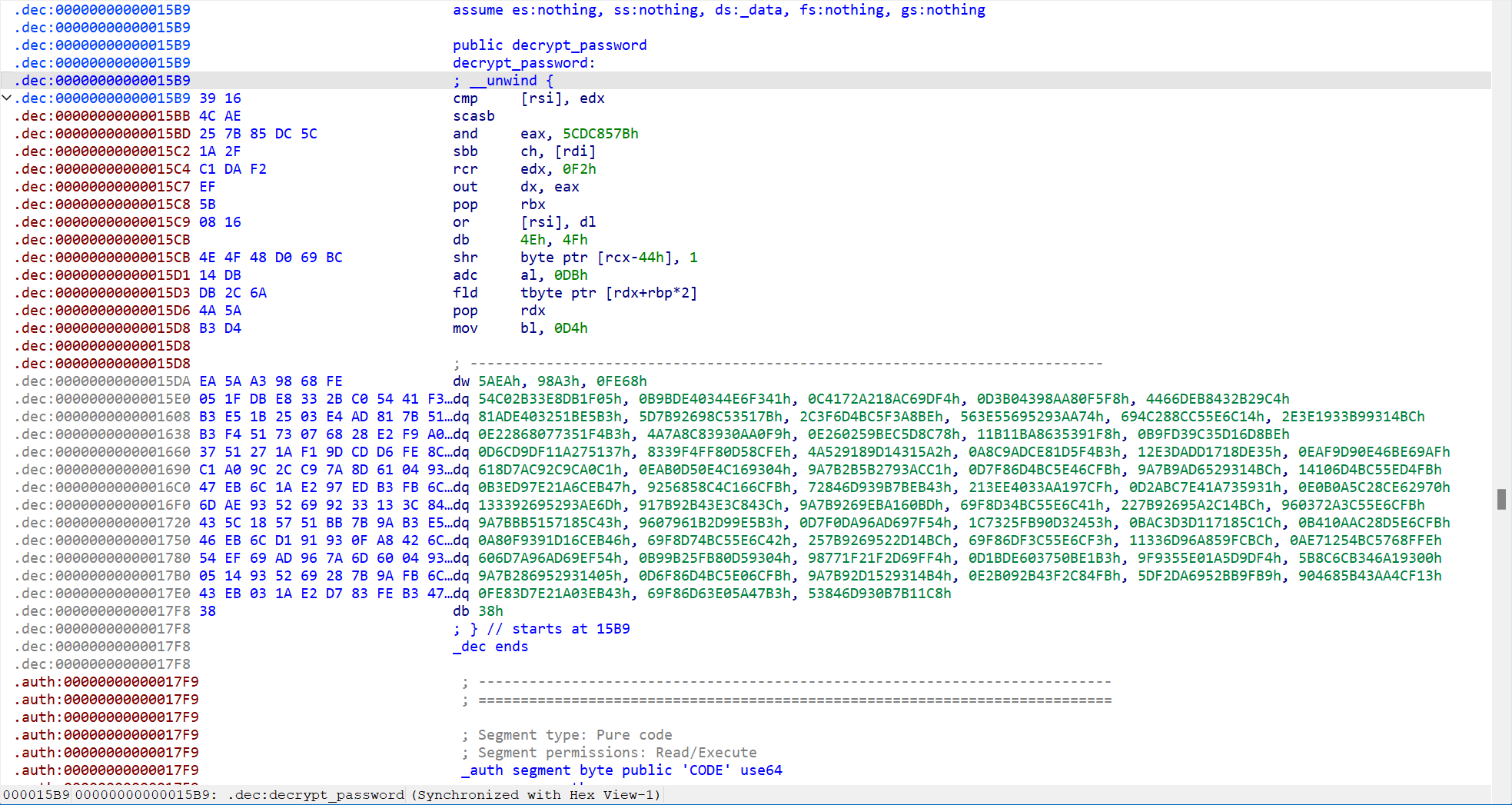
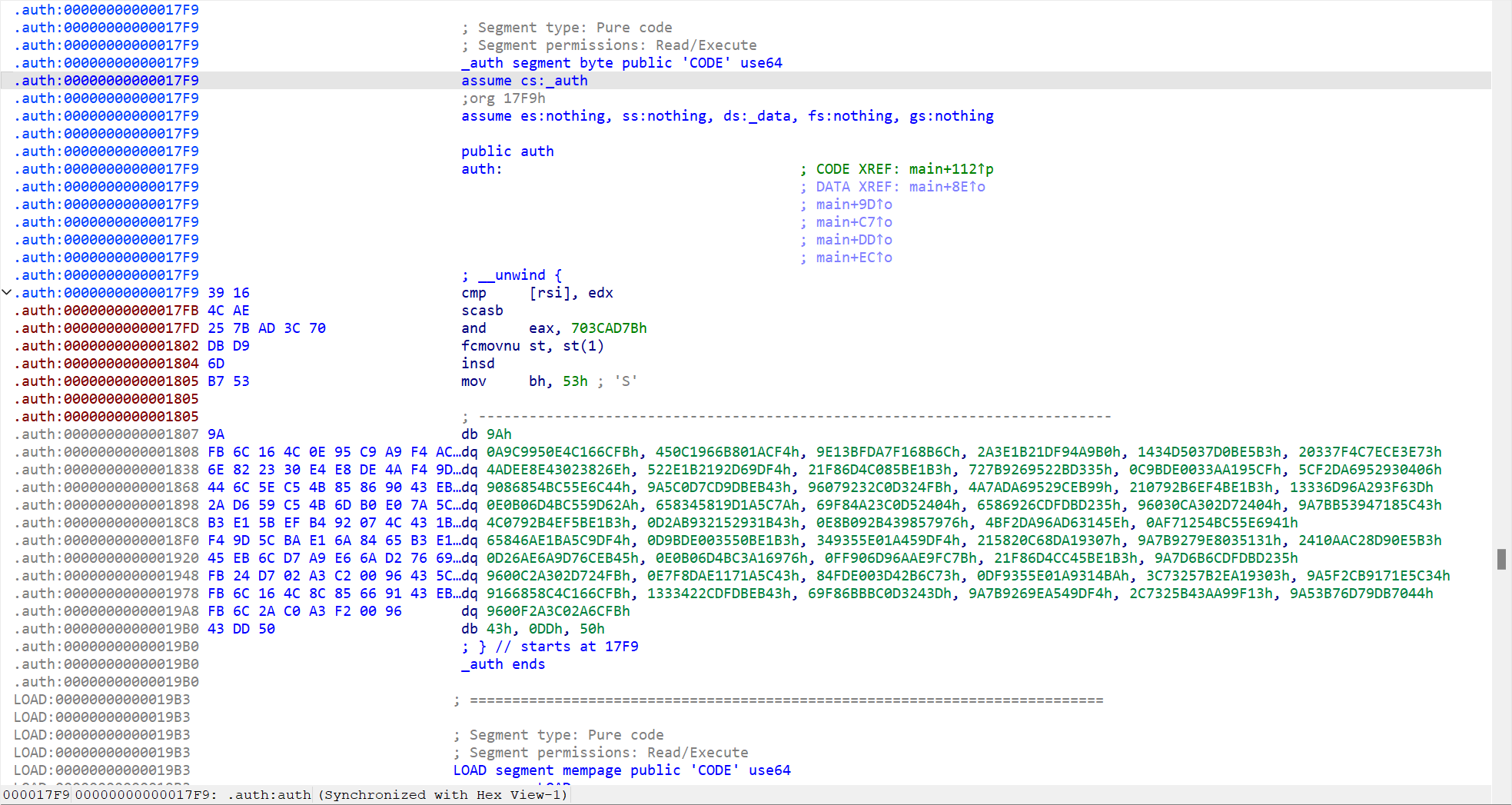
可以看到应该是有SMC
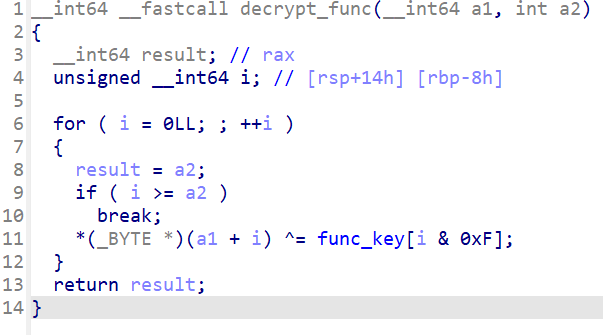
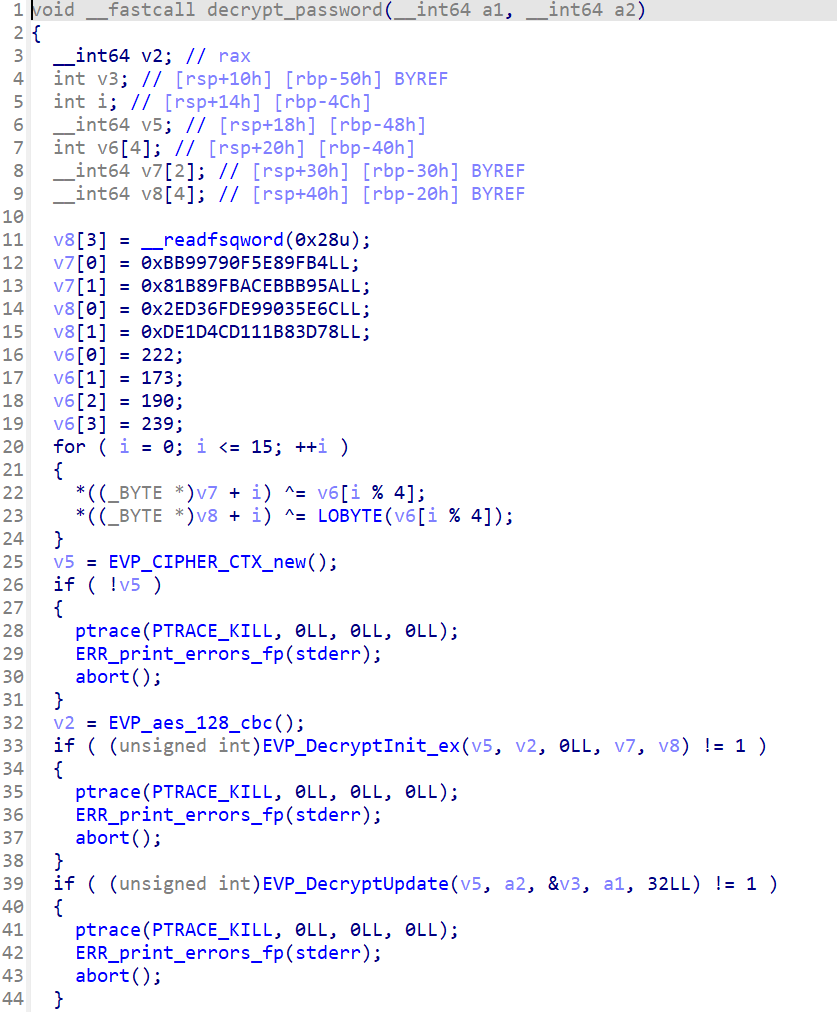
decrypt_func 函数如下
到汇编界面可以看到 0x15B9到0x17F8和0x17F9到0x19B0是被加密的代码
使用idapython 脚本patch一下
1 | addr = 0x15B9#0x17F9 |
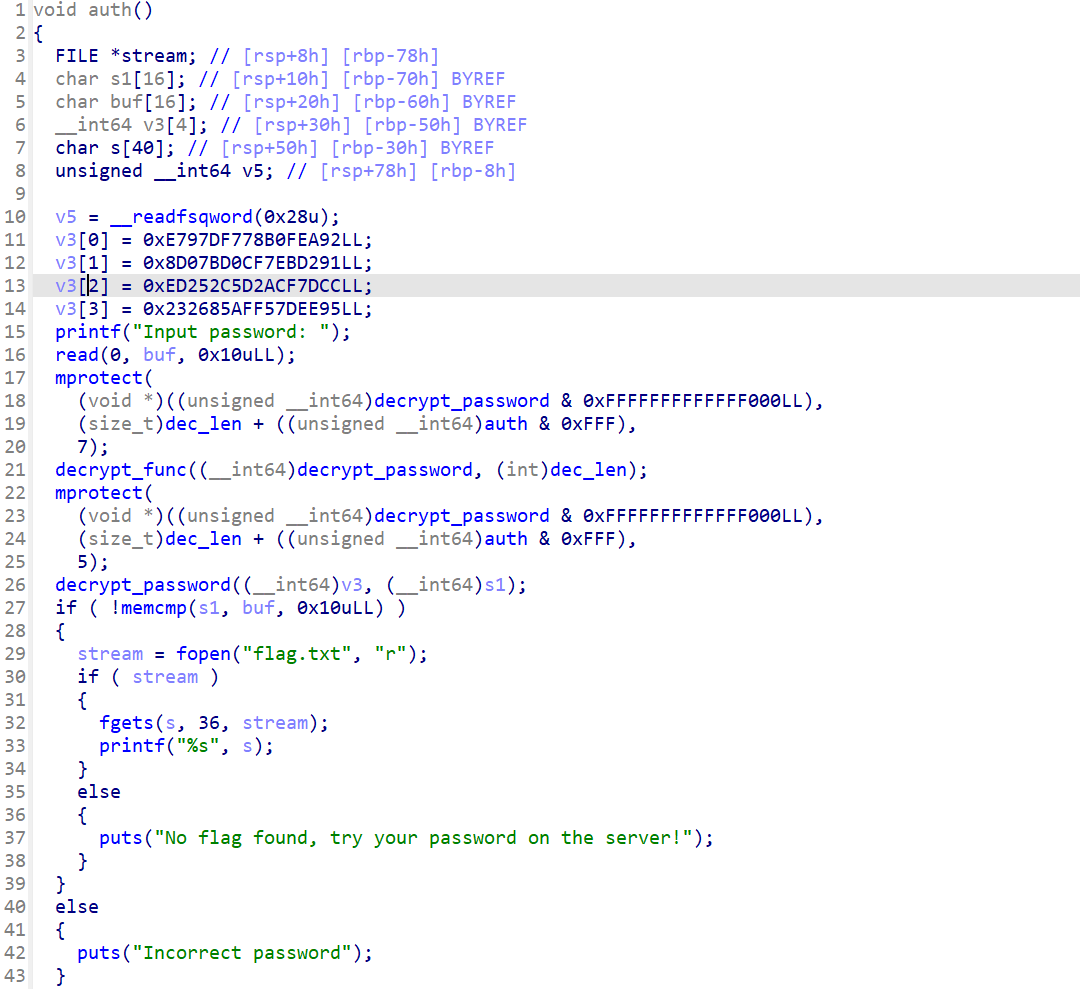
解出来以下两函数,看了大概逻辑感觉应该能动调获取密钥
nop绕过一下check_Debug,然后再memcmp前下断点,看看传入的参数
得到密钥N0tUrM0msP4sswd!
flag
gigem{a_b4ttl3_4_th3_hist0ry_b00ks}
Alien
描述:
Run the lm3s6965 firmware. Press enter to let it know you’re listening. Read the flag.
根据描述,这是个lm3s6965的固件
搜索得知可以用 QEMU 运行
嵌入式Rust之书
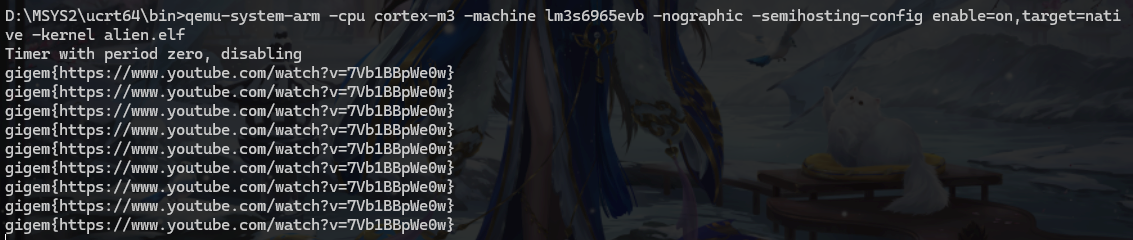
跟着教程安装好QEMU后,直接运行
1 | qemu-system-arm -cpu cortex-m3 -machine lm3s6965evb -nographic -semihosting-config enable=on,target=native -kernel alien.elf |
flag
gigem{https://www.youtube.com/watch?v=7Vb1BBpWe0w}